What Are AWS Gravitron Processors?
Data centers are quickly becoming more diverse. For years, it was Intel or nothing and then AMD made inroads with its EPYC processors. But in the past few years, ARM has become a hot new commodity.
Along with ARM, large companies like Apple, Microsoft, Google and Amazon have been designing their own chips. And with ARM being easily accessible for these companies, it makes sense that they would use this architecture for their in-house designed chips.
Amazon’s Graviton processors fall right into this category and are built around Arm cores and are custom-built chips that the company says are designed for performance and cost. The ideal use-case for these processors are micro services, web servers, development environments, and caching fleets.
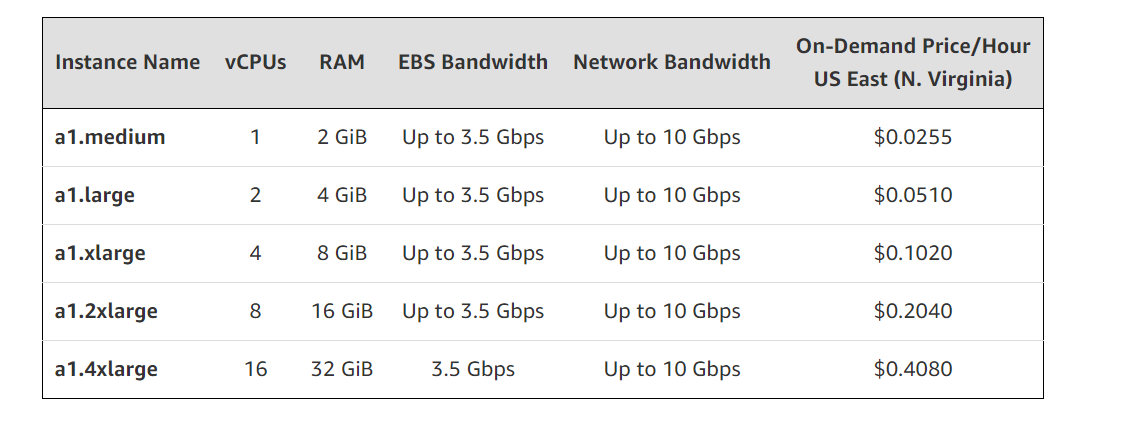
Amazon has five sizes of a1 instances available and are EBS-Optimized by default:
If your application is written in one of the many scripting languages, there is a high probability that you can move over to these A1 instances and run your application without any additional coding required. It should be a simple drag and drop and off you go.
These instances are available now in the US and will spread out as demand is increased for these types of workloads. While not everything should be run on ARM-based servers, for those that need this functionality,