How to Find Out Which Users Are Logged on Windows Server
Apart from trailing through the event logs, Windows Server doesn’t include any easy, built-in way to find out which users are logged in locally to a server. It’s often useful for system administrators to know which users are logged in locally to a server or just remotely accessing resources, whether for troubleshooting purposes, reporting or some other kind of investigation. In this Ask the Admin, I’ll show you how to find out which users are accessing remote resources and which are logged in locally.
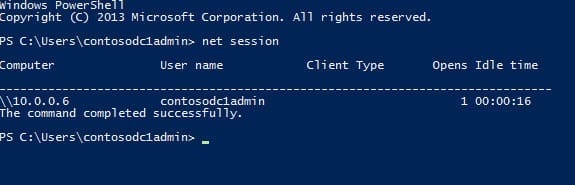
Enumerate Users Remotely Accessing Server Resources
Fortunately it’s easy to get a list of remote users accessing server resources. Start by opening a command prompt with local administrator permissions. These instructions will work on all currently supported versions of Windows Server.
- Right-click the PowerShell icon on the desktop taskbar and select Run as Administrator. Enter administrator credentials if prompted.
- In the PowerShell prompt, type net session and press Enter.
A list of users, and the IP addresses from which they are accessing resources on the server, will be displayed.
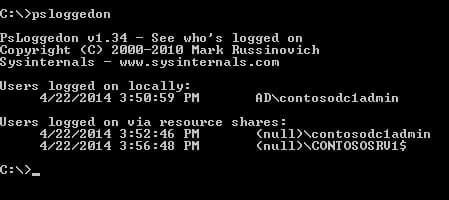
List Users Logged in Locally to a Remote Server
To get a list of users logged in locally to a server, we’ll need to use psloggedon, a tool that can be downloaded free from Microsoft’s website. Once the PS tools are downloaded, extract the zip folder and copy psloggedon.exe to the directory where you want to run the tool.
- Log on to the server as a local administrator.
- Open a command prompt by typing cmd on the Start screen and pressing Enter.
- Make sure the command prompt working directory is the same as the location of psloggedon.exe. You can change the working directory by using the cd command. For example, type cd c:\pstools\ and press Enter to change the working directory to pstools in the root of the C drive.
- In the command prompt window, type psloggedon and press Enter.
This will display all the users logged on locally to the server and users accessing resources on the server but not logged on locally. Additionally, you can specify a computer name to list the users logged on to a remote server, replacing contosodc1 with the name of the remote server:
psloggedon \\contosodc1
You can also search the network for a given user. Type the following command, replacing contosodc1admin with the username you want to search for:
psloggedon contosodc1admin