Understanding Hybrid Azure Active Directory Join
Understanding the concept of joining a device to a Windows Server Active Directory domain, otherwise known as Active Directory Domain Services (ADDS), is fairly easy to grasp. But with the arrival of Windows 10 and Azure Active Directory (recently renamed Microsoft Entra ID), it’s fair to say that everything is more complicated.
AAD is Microsoft’s cloud-based identity management solution. It was designed to provide identity management for cloud-first applications, like Office 365. ADDS can be extended to the cloud by synchronizing accounts to AAD. AAD Connect synchronizes accounts so that the same credentials can be used to sign in to on-premises ADDS and cloud apps, like Office 365, that use AAD for user authentication.
Windows 10 and Azure Active Directory
Windows 10 devices can be joined to AAD. In this case, users sign in to Windows 10 using their AAD credentials. Windows 10, and operating systems that don’t support joining AAD domains, like iOS, Android, macOS, and Windows 7 can be registered with AAD instead.
AAD registration is primarily designed for Bring Your Own Device (BYOD) scenarios. Users sign in with a local account, or Microsoft Account (MSA) on registered devices. Registration provides seamless sign-on (SSO) to cloud resources much like devices that are joined to AAD.
At first glance, it might seem that there isn’t much difference between AAD join and registration. But if AAD joined devices can access domain controllers, and your ADDS domain is synchronized to AAD using AAD Connect, devices also get SSO to resources and applications that use ADDS and Windows-Integrated authentication. For example, you could access a UNC path, or web server configured for Windows-integrated security, on an AD member server from a device that is joined to AAD.
Hybrid AAD Join
If you need access to ADDS and AAD without any restrictions, then a hybrid AAD join is the solution. Devices hybrid joined to AAD are not joined to AAD. But instead, joined to ADDS and automatically registered with AAD. Users sign in to Windows using their ADDS credentials.
Service connection points
Before you can use hybrid AAD join devices, ADDS must be synchronized to AAD using AAD Connect. AAD Connect uses a wizard to set up hybrid AAD join, including configuring the service connection points (SCP) in ADDS that are required for device registration to AAD.
Each AD forest requires its own SCP. Because AAD registration happens automatically for hybrid AAD joined devices, an SCP is required to locate information about your AAD tenant during the registration process.
The SCP is registered in AD as a container under CN=Device Registration Configuration. In the properties of the container, there is an attribute called ‘keywords’ containing two strings that Windows 10 uses to locate your AAD tenant.
Computer accounts and certificates
When Windows 10 devices see the SCP in ADDS, they begin trying to register with AAD. But registration can’t be completed until a couple of other conditions are met. First, the device’s computer account must be synchronized from ADDS to AAD. By default, AAD Connect synchronizes objects every 30 mins.
Secondly, AAD Connect won’t sync the computer object until its userCertificate attribute is populated with a self-signed certificate generated by the device itself. But regardless of whether the computer object has synchronized to AAD, the device tries to register with AAD, resulting in a failure.
When the device successfully registers with AAD, you’ll see Event ID 306 in the User Device Registration log: ‘Automatic registration Succeeded’. Once registered, users are also issued an Azure AD primary refresh token (PRT) that can be used to authenticate to services that use AAD.
If the user logs in before AAD registration has completed, they will need to either sign out and back in again, or lock and then unlock the device, to authenticate with AAD.
Down-level Windows devices
Support for hybrid Azure AD join can also be extended to Windows 7 and Windows 8.1. But because these operating systems don’t natively support AAD registration, you must install Microsoft Workplace Join for non-Windows 10 computers.
Additionally, use of down-level Windows devices requires a couple of extra configuration steps. The following URLs must be added to the local intranet zone in Internet Explorer to avoid certificate prompts:
- https://device.login.microsoftonline.com
- https://autologon.microsoftazuread-sso.com
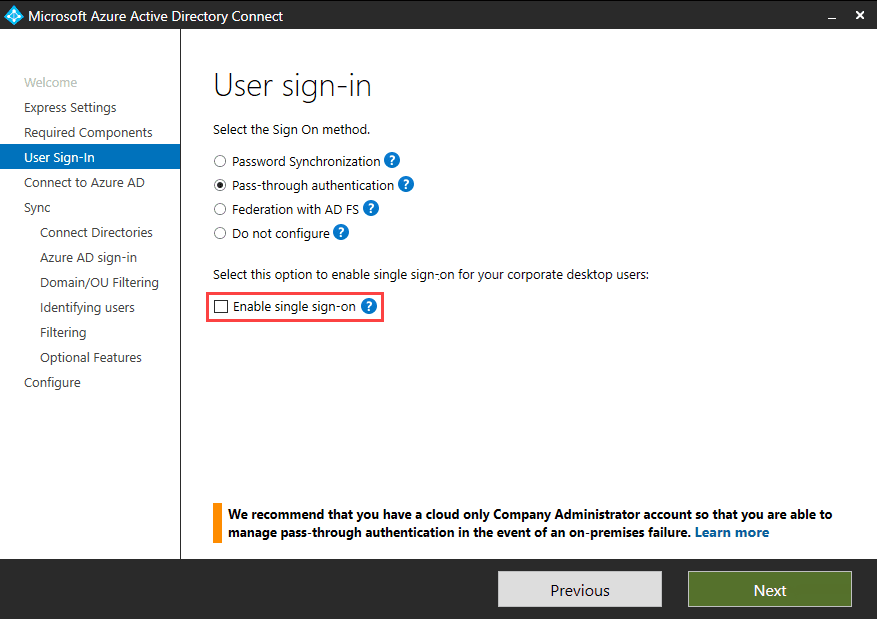
Allow updates to status bar via script in the user’s local intranet zone must also be enabled. When using password hash synchronization or passthrough authentication (PTA) with AAD Connect, Enable single sign on must also be checked on the User sign-in screen.
For more information on configuring hybrid Azure AD join using AAD Connect, see Microsoft’s website here.
Active Directory Federation Services
The process I described above for hybrid Azure AD join is for situations where organizations configure AAD Connect to use password hash synchronization or PTA. Both these methods are recommended by Microsoft in favor of Active Directory Federation Services (ADFS).
The ADFS process for hybrid Azure AD join doesn’t need the computer object’s userCertificate attribute to be updated or synchronized to AAD. ADFS creates the computer object in AAD and sends a certificate to the device, allowing AAD registration to complete much faster.
Despite the speed in which AAD registration completes with ADFS, you should still use password hash synchronization or PTA with AAD Connect. Microsoft is working on making the AAD registration process faster for organizations not using ADFS.
For more information on setting up PTA with AAD Connect, see Set Up Azure Active Directory Connect Pass-Through Authentication on Petri.