System Center 2012 SP1 – Orchestrator: Sample Runbook Restrictions
The final step in our three-part sample series illustrating the flexibility of combining the modules and components of System Center 2012 SP1 -Orchestrator with the free portal from ITQ – the EUPSCO (End User Portal for System Center Orchestrator) – we are going to address the added step that we should execute to restrict access to our services to only the group of people with whom the offering is relevant.
(Editor’s note: In case you need to catch up, the other two articles in this sample series are: System Center 2012 SP1 – Orchestrator: Sample Runbook Creation and System Center 2012 SP1 – Orchestrator: Sample Runbook Publishing.)
System Center 2012 SP1 – Orchestrator and Restricting the Service
To implement the restrictions, we are going to use a regular security group from Active Directory.
AD Group
In my sample environment I have created a group called “!HR Team” and added the user which we created while validating the scenario in our last post as a member of this group.
EUPSCO
Next, open your browser and log into the EUPSCO portal, with administrative credentials
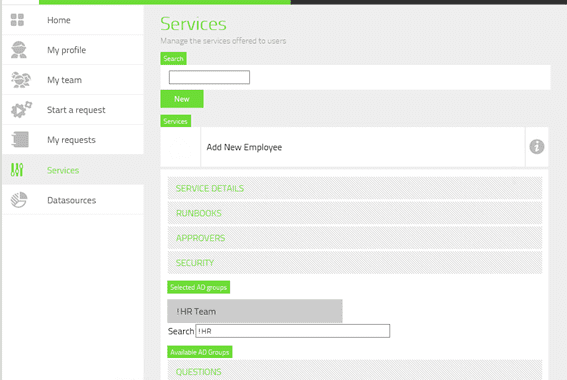
- Click on the menu item Services to be presented with the list of services you have defined.
- From this list, select the service you wish to restrict, for example “Add New Employee.”
-
The page will update listing the five configuration categories available for the service. Click on the Category Security.
-
In the Search field, enter the string you plan to match (for example, !HR).
-
The page will update and you should see a list of matching groups presented under the heading Available AD Groups.
-
Click on the desired group from this list to select it, moving it to the Selected AD Groups list.
- Finally, you can click Save to update the service with our new restriction.
Testing the Restriction
Still logged in as Administrator, we will check to see if we still have access to the service. In my environment the Administrator is not a member of the !HR Team group, so I expect that the service should not be available to select
- From the Menu, select the option Start Request.
-
On the first page, again you need to select the User on whose behalf you are executing the service.
-
By default there is only one user, MySelf, so simply click this user for it to be automatically moved under the heading Selected Users, then click Next.
- Assuming that the restriction has worked and you have not published any other services, then there will be no services available to choose from on the second page.
Neat! At this point, it appears that we have at least hidden the service from users who do not fall within the access scope
HR Team Member
Log into a workstation with the credentials of a member of the HR team, then launch their browser, and connect to the EUPSCO portal. You will be presented with a subset of the options that were available while you connected with administrative credentials.
- From the Menu, select Start Request.
-
On the first page, you need to select the user on whose behalf you are executing the service.
-
By default there is only one user, MySelf, so simply click this user for it to be automatically moved under the heading Selected Users, then click Next.
-
On the second page, you will see a list of all the services that are available for the user we just selected. As this is our first and only service, you should now see its entry.
-
Click the service Add New Employee and it will move under the heading Selected Services. Then click Next.
We don’t need to continue, as now we know that the service is indeed available for us to select and use.
Final Thoughts
As you can appreciate, the flexibility of our new portal is amazing, there is very little configuration required, and with the simple process of just assigning a security group to a service to control its access, this portal will provide a very simple and seamless interface for users to integrate with our runbooks until such time as we get our service manager online and configured.
Note: I should point out, that during testing I did have some initial problems with saving the security group to the service while using IE 10, but switching over to Chrome instantly resolved that issue. These appear to be little issues with the parsing of HTML 5.0