Solving Group Policy Problems with the Group Policy Results Wizard
Sometimes referred to as Resultant Set of Policy (RSoP), in this Ask the Admin, I’ll show you how to determine which Group Policy settings are actually being applied to devices using the Group Policy Results Wizard.
Group Policy Results is a feature of the Group Policy Management Console (GPMC), and allows administrators to scan the local or remote machines, and users to determine which Group Policy objects (GPOs) and settings are being applied. This differs from Group Policy Modelling, which shows the result of applying a set of GPOs without making any changes to users or machines.
The Group Policy Results Wizard helps system administrators figure out what settings are really being applied to devices, which can be a difficult task when you consider that multiple GPOs might be linked at different levels of the AD hierarchy, then add different processing options and enforcement settings, along with WMI filters, and it may not be immediately clear what settings are being applied.
Group Policy Management Console
The Group Policy Management Console is installed by default on all Active Directory domain controllers (DCs). Alternatively, GPMC is installed as part of the Remote Server Administration Tools (RSAT) for Windows Server 2012 R2, which are supported on client and server versions of Windows. For details on RSAT, see Remote Server Administration Tools (RSAT) for Windows 8: Download and Install on the Petri IT Knowledgebase.
Setting Up Your Environment for RSoP
Before analyzing remote devices, you’ll need to make sure that the relevant inbound Windows Firewall rules are enabled for Group Policy Results. Windows Firewall includes a set of built-in rules for Group Policy Results that need to be enabled for GPMC to make connections to remote machines. The Windows Firewall rules are Remote Event Log Management (NP-in), Remote Event Log Management (RPC), Remote Event Log Management (RPC-EPMAP), and Windows Management Instrumentation (WMI-in).
But don’t worry, it’s easy to enable the Windows Firewalls rules on all devices in your domain using Group Policy, because there’s a starter GPO included in Windows Server 2012 (and later) that includes the necessary settings. For more information on using starter GPOs and linking GPOs, see How to Use Starter Group Policy Objects in Windows Server and How to Create and Link a Group Policy Object in Active Directory on Petri.
Alternatively, you can quickly create a GPO with the necessary settings, and link it your domain so that it applies to all devices, using the PowerShell cmdlet below. You’ll need to log in to a domain controller as a domain administrator, or a device that has the Active Directory module for PowerShell installed, to run the cmdlet. Don’t forget to replace dc=ad,dc=contoso,dc=com in the –target value with the CN of your domain name.
New-GPO –Name ‘Windows Firewall RSoP Ports’ –StarterGpoName ‘Group Policy Reporting Firewall Ports’ | New-GPLink –target ‘dc=ad,dc=contoso,dc=com’ –LinkEnabled yes
Group Policy Results Wizard
Now that the necessary Windows Firewall rules have been applied to devices in the domain, let’s open GPMC and check the Group Policy settings on a device.
Log on to a Windows Server 2012 R2 domain controller (DC) using a domain administrator account, or a device where RSAT is installed.
- Switch to the Start screen, type group policy management and select Group Policy Management from the search results.
- If you need to start GPMC with alternate user credentials, make sure Group Policy Management is selected in the search results, press CTRL+SHIFT+ENTER and then enter a username and password.
- In the left pane of GPMC, expand your AD forest, right click Group Policy Results in the left pane, and select Group Policy Results Wizard from the menu.
- Click Next in the Group Policy Results Wizard on the welcome screen.
- On the Computer Selection screen, check Another computer.
- In the box, type a computer name. Alternatively, click Browse and use the Select computer dialog to select a computer account.
- Click Next on the Computer Selection screen.
- On the User Selection screen, if you want to also collect user results, check Select a specific user and then select a user from the box. The box only displays users that have logged in previously to the remote device.
- If you’re not interested in collecting the results of user policy, check Do not display user policy settings in the results (display computer policy settings only). Click Next to continue.
- Check the configured settings on the Summary of Selections screen and click Next.
- Click Finish in the Group Policy Results Wizard window.
Note that at this point, you have the option to rename the results report in the left pane, or you can just press ENTER to accept the default name.
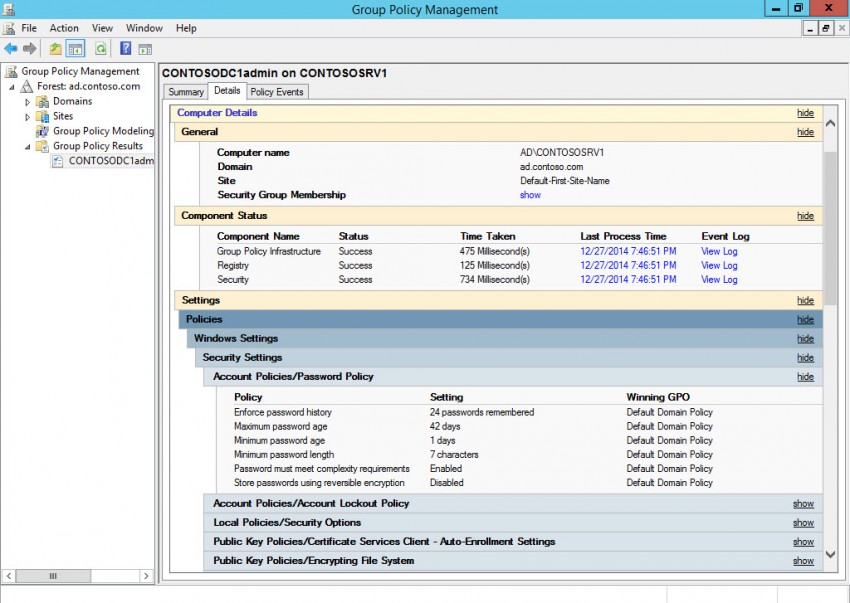
The Report
On the Summary tab in the right pane of GPMC, you should see a message saying No Errors Detected for both computer and user policy. Now switch to the Details tab. Here you’ll find the nitty gritty of the report. In this example, I can see information about GPO processing at the top of the Details tab. The GPOs applied to the device, in this case CONTOSOSRV1, are listed along with any WMI filters that are applied. Under Computer Details and User Details respectively, you can expand the relevant sections to see the actual settings that are applied to the remote device.




