Sensitivity Labels Exert More Control Over SharePoint Online Sites
Expanding the Control of Sensitivity Labels
In a Teams live event to brief customers on July 14, Microsoft revealed details of how they plan to evolve the container settings in sensitivity labels to exert more control over SharePoint Online sites. Microsoft also plans to improve the flow of creating new sensitivity labels to create “label scope” or the ability to target a label to apply to containers, documents and email, or both. The new creation flow and scoping is due to arrive in tenants in early August and I’ll cover that in another article.
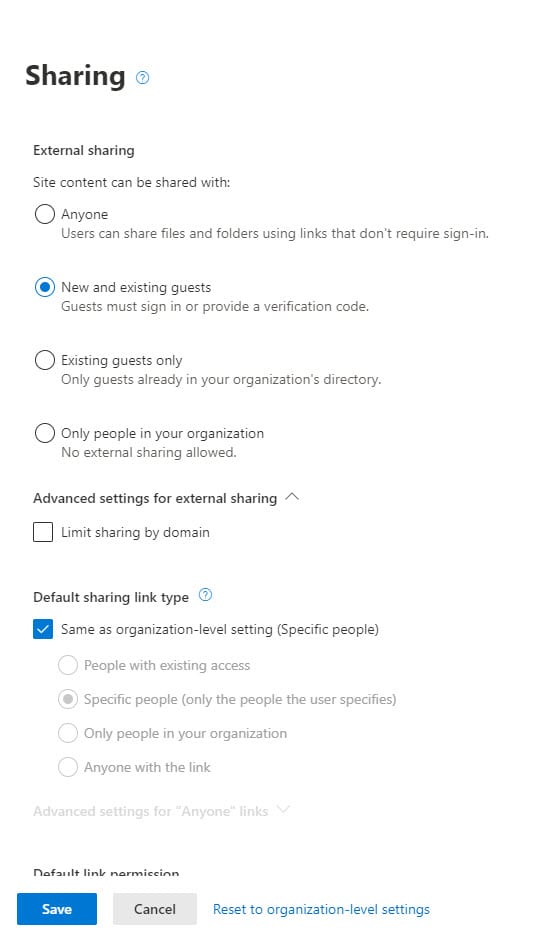
When Microsoft introduced the ability of sensitivity labels to control container settings, a limited number of controls were available. You can create a label which, when applied to a team, site, or group, bars access to guest members or sets the access to be public or private (or decided by the container owner), or limits access to documents in a SharePoint when using unmanaged devices. The current controls are useful, but the intention always was to expand the number of controls to make sensitivity labels a much more powerful method to exert policy over containers. This is what we now see unfolding.
Controlling Access to SharePoint Online Sites
SharePoint sites often store many sensitive documents. Users can protect those documents by manually applying sensitivity labels. Tenants can use auto-label policies to find sensitive documents and apply labels in bulk (an E5 feature). It’s a natural step to enable labels to control access to documents in sites where the overall content is deemed confidential or sensitive. The container controls available in sensitivity labels are being extended to:
- Controlling sharing capability for sites. This capability will be available very soon, but only in PowerShell. The user interface to set sharing capability by label will come later in the Microsoft 365 compliance center.
- Controlling access to a site by requiring multi-factor authentication (see this article). This will be done by linking sensitivity labels to Azure AD conditional access policies so that a label applied to a site can require users to authenticate with MFA (and agree terms of use) before SharePoint allows them to access documents. This capability will come in later 2020.
Today, SharePoint Online and site administrators can set the sharing capability for a site through the SharePoint admin center (Figure 1).
Updating Sharing Capability with PowerShell
You can also set the sharing capability with PowerShell by running the Set-SPOSite cmdlet:
Set-SPOSite -Identity $SiteURL -SharingCapability Disabled
SharePoint Online supports four values for sharing capability:
- Disabled – no external sharing outside the organization is allowed.
- ExistingExternalUserSharingOnly – allow sharing only with the guest users already in your organization’s directory.
- ExternalUserSharingOnly – allow users to share documents with new external users, who must accept the sharing invitations and go through an authentication process to create a guest account.
- ExternalUserAndGuestSharing – allow sharing with all external users, and by using anonymous access links (Anyone links).
Not every site owner knows how to use admin tools to change site settings, so the advantage of tying sharing capability to labels makes it easier for a site owner to control how sharing works for their site by switching labels. The logic here is that site owners know and understand the material stored in the site better than anyone else, so they should be able to select the most appropriate label through the Site Information panel and, by extension, the right sharing capability.
Adding Sharing Capability Control to Sensitivity Labels
To upgrade a sensitivity label to control sharing capabilities for SharePoint Online sites, we use the Set-Label cmdlet, which is available after you connect to the Security and Compliance endpoint.
Not all sensitivity labels have settings for containers, so to find the set that we can use with sites, you can run this code:
$Labels = Get-Label
ForEach ($Label in $Labels) {
$LabelActions = $Label.LabelActions | Convertfrom-Json
ForEach ($LabelAction in $LabelActions) {
If ($LabelAction.Type -eq "protectgroup") {
Write-Host "Label" $Label.DisplayName "has container actions" }
}}
With the knowledge of what labels are used with containers, we can go ahead and update the labels we want to control sharing capabilities. This is done by updating a label’s advanced settings. For example, let’s assume that we want any site labelled as Public to allow anyone links. This is done with:
Set-Label -Identity Public -AdvancedSettings @{sharingcapability="Anyone"}
Remember that you can’t assign a less restrictive access to a site than allowed by the tenant sharing setting. In other words, if the tenant explicitly blocks anyone access for all sites, assigning anyone access through a label will have no effect.
Here’s two other examples. In the first, we limit sharing for sites labelled as Confidential to existing guest accounts. The second disables access to sites labeled as Secret. You can also use the label GUID (identifier) instead of the label name.
Set-Label -Identity Confidential -AdvancedSettings @{sharingcapability="ExistingExternalUserSharingOnly"}
Set-Label -Identity Secret -AdvancedSettings @{sharingcapability="Disabled"}
After updating a label with a sharing capability setting, if you apply the label to a site, its sharing capability is updated. You can check that the settings have changed with the Get-SPOSite cmdlet:
Get-SPOSite -Identity $SPOSite | Select SharingCapability, SensitivityLabel
SharingCapability SensitivityLabel
----------------- ----------------
Disabled 27451a5b-5823-4853-bcd4-2204d03ab477
Checking that Everything Works
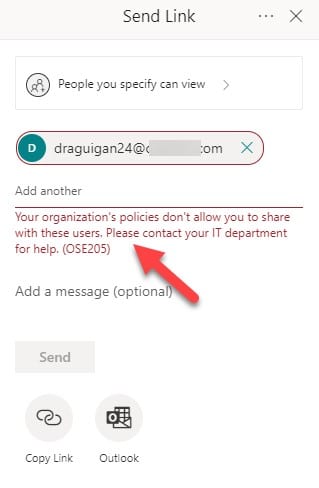
If you have the site open, you should refresh it to make sure that SharePoint Online picks up the new setting and then check that document sharing works as expected. For instance, if someone tries to share a document with an external user when sharing is disabled, they should be blocked (Figure 2).
Progress but Still Room to Improve
Adding extra controls for sites to sensitivity labels is a strong indication of how Microsoft wants to develop the capabilities of labels to make them more useful and powerful. Although applications are steadily embracing sensitivity labels (Power BI is the latest), what’s missing in the container story is the lack of support in some Office 365 applications, notably Yammer and Planner. Both are longstanding outliers in the Office 365 compliance story, with Yammer only recently supporting the capture of compliance records for messages (and only for networks configured in modern Microsoft 365 mode). Planner seems blissfully unaware of what’s happening around it in terms of compliance processing.
It would be nice if Microsoft could expand coverage of sensitivity labels to protect data across the complete Office 365 suite. We can but dream…