Speaking to a large crowd of security professionals at the RSA Conference 2013 in San Francisco this morning, Microsoft Corporate Vice President of Trustworthy Computing Scott Charney argued that despite the almost daily reports of data breaches and cyberattacks on companies and governments that the audience was getting accustomed to reading about, the security industry had made great strides towards combating cyber attacks in recent years.
In a blog post timed to coincide with his RSA keynote, Charney writes that the industry is much more well prepared than the constant drumbeat of headlines discussing cyber attacks and data breaches. “In the midst of sometimes provocative headlines, the tangible progress being made to advance the industry is often overlooked…however look at the breadth of the good work that industry and government is doing, I’m encouraged.”
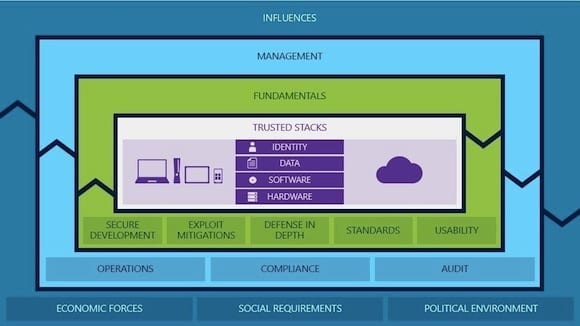
A slide from Charney’s RSA Conference 2013 keynote, visually demonstrating aspects of Microsoft’s Trustworthy Computing model.
Charney lumped the areas the industry had made progress in into three large groups, which he dubbed fundamentals, influences, and management. Fundamentals cover how computers, smartphones and tablets are engineered and added to an IT infrastructure, while influences deal with outside forces — like the larger economy, state, federal, national, and international politics — that have an impact on IT security. Management is focused on the basic blocking and tackling of security operations, and Charney made the case that great strides have been made in all of these areas.
Charney mentioned the Unified Extensible Firmware Interface (UEFI) as being one of the tools that are helping make PCs safer and more secure. UEFI allows PCs to be configured to have a trusted boot process which improves protection against malware, root kits, and other hostile software. While Charney made a compelling argument that the industry has made compelling security progress, he did point out that the four most common security threats are currently arriving in the form of corporate espionage, cybercrime, military espionage, and outright cyberwarfare.
Charney closed his keynote by describing security optimism as a “future state…[where] we can be less reactive, and more predictive” and that all of the improvements he’s described contribute to placing the industry on the cusp of achieving that reality. You can watch Charney’s keynote in it’s entirety via the RSA Conference keynote archives.
Are you attending the RSA Conference in San Francisco this week? Add a comment to this blog post and let me know what you think of the conference so far.
- Follow Jeff James on Twitter (@jeffjames3) and Google+ (add Jeff to your circles)
- Follow Petri IT Knowledgebase on Twitter (@petri_co_il)
- Follow us on Facebook and Google+ as well!