Remotely Enable Remote Desktop on Windows Server 2003
- Blog
- Networking
- Post
With Remote Desktop on Windows XP Professional or Windows Server 2003 (in Windows 2000 Advanced Server, this feature was called Terminal Services in Remote Administration Mode), you can have access to a Windows session that is running on your computer when you are at another computer.
What you need to do is create the new RDP listening port via the registry:
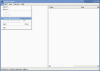
- Run REGEDIT on your XP workstation or on your Windows 2000/2003 Server.
- Click on File, then choose “Connect Network Registry”.
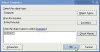
- In the Select Computer search box either browse Active Directory to locate the remote server, or type its name in the dialog box.
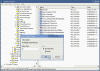
- In the remote machine’s registry browse to the following key:
HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server
- Under the Terminal Server key find the value named fDenyTSConnections (REG_DWORD). Change the value data from 1 (Remote Desktop disabled) to 0 (Remote Desktop enabled).
- Close Regedit.
- Reboot the remote machine for the change to take effect. You can easily do so by opening a command prompt and typing the following command:
shutdown -m \\srv1 -r
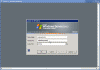
After the remote machine reboots, Remote Desktop will be enabled on it. To test this from your workstation, open Start -> All Programs -> Accessories -> Communications -> Remote Desktop Connection. You can also type mstsc in the Run command.
Enter the name of the remote server in the Remote Desktop Connection logon box, supply your administrator password when prompted, and press Enter or click Ok.
Related articles
You might also want to read the following related articles:
- Add a new RDP Listening Port to Terminal Server
- Change Terminal Server Listening Port
- Download RDP 5.2
- Download Remote Desktop Web Connection for XP SP1
- Enable Remote Desktop on Windows Server 2003
- Install Remote Desktop Web Connection on Windows XP
- Install Remote Desktop Web Connection on Windows Server 2003
- Securing RDP/Terminal Services Communications
- Offer Remote Assistance in Windows XP/2003
- Quickly Connect to Remote Computers
- Use RDP Client to Connect to a Different Port
- Use Terminal Server Client to Connect to a Different Port
- What’s Remote Desktop in Windows XP/2003?
- What’s Remote Assistance in Windows XP/2003?