Performing an Offline Domain Join in Active Directory
How do you perform an offline domain join in Active Directory?
Microsoft introduced the offline domain join tool (Djoin.exe) in Windows 7 and Server 2008 R2, allowing system administrators to join Windows server or client operating systems to an Active Directory (AD) domain when there’s no connectivity to a domain controller (DC). There are a couple of scenarios where this can come in handy. First, domain join operations don’t always work reliably over wide-area network connections, even when there is connectivity to a remote domain controller. Second, offline domain joins can be performed as part of an unattended Windows installation. You should note that use of the offline domain tool is not supported on VMs that use differencing disks generated from a master Windows image.
There are two steps to the offline domain join process: provisioning a computer account in AD (djoin /provision) and then joining the desired computer to AD (djoin /requestODJ). To provision a computer account in AD, you must have connectivity to a DC. The Djoin.exe tool can only be run on Windows 7 and Server 2008 R2 (or later).
Provision a computer account in AD
- Logon to any Windows 7 or Windows Server 2008 R2 (or later) computer that is a member of the domain. The account you logon with must have permission to add workstations to the domain — for instance, a Domain Administrator.
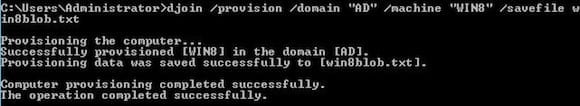
- Open a command prompt and run the following command: djoin /provision /domain “AD” /machine “WIN8” /savefile win8blob.txt
Replace AD with the netbios name of your domain, then replace WIN8 with the machine name of the computer you want to join to the domain. The BLOB file that Djoin saves is required by the machine that you want to join to the domain and should be named appropriately. If you don’t have any Server 2008 R2 (or later) DCs in your domain, you need to additionally specify the /downlevel switch.
If the djoin /provision command completes successfully, you’ll see a new computer account in the Computers container in AD. Before you can join your offline machine to the domain, it must have access to the BLOB file created by the djoin /provision command.
Perform an offline domain join
- Logon to the machine that you want to join to the domain with a local administrator account and open a command prompt with elevated privileges.
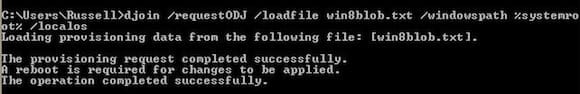
- Run the following command and replace win8blob.txt with the name of the BLOB file you created with the djoin /provision command: djoin /requestODJ /loadfile win8blob.txt /windowspath %systemroot% /localos
- Reboot the machine.
The /localos switch is required when running djoin /requestODJ on an online image. Offline domain joins can also be performed against offline virtual hard drive (VHD) images.
Once the machine has rebooted, if you go to System Information in the Control Panel, you’ll see that the computer is now a member of your domain. Remember that you’ll only be able to logon with a domain account for the first time if there’s connectivity to a DC.