Using Office 365 Data Loss Prevention (DLP)
Nearly every day we hear news of disastrous leaks of sensitive data that ranges anywhere from customer credit cards to social security numbers. Often these breaches aren’t the result of sneaky attackers subverting security measures, but from simple oversights by well-meaning employees. Even if accidental loss of important data in your organization wouldn’t make the news, you’ll still want to take a look at some of the Data Loss Prevention (DLP) tools provided by Microsoft in Exchange 2013 and Exchange Online.
Note: Keep in mind that as a premium feature, DLP will require an Exchange Online Plan 2 subscription with Office 365 or an Exchange Enterprise Client Access License (CAL) for on-premise Exchange. See our article on choosing an Office 365 subscription plan for more information.
Using DLP with Office 365 Exchange Online
Data Loss Prevention (DLP) is a policy management system that helps you identify sensitive data leakage within outgoing email. The system also intervenes to prevent accidental data loss. Based on the existing and well-proven transport rule feature, each policy consists of conditions, actions, and possible exceptions that determine how emails containing sensitive data are handled. In this way, they are similar to setting up Transport Rules or Inbox rules.
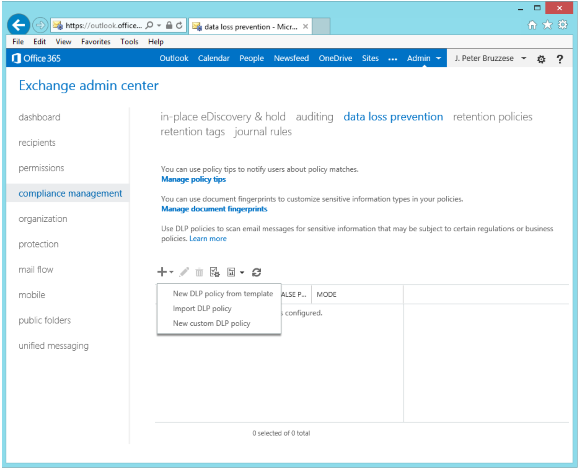
Data loss prevention settings in the Office 365 Exchange admin center.
(Image: J. Peter Bruzzese)
Microsoft provides several template DLP policies that will help you identify data that’s subject to known laws, such as HIPPA. You can also create your own custom policies or import one created by a trusted third party. When setting up your own policies, you can identify sensitive information using one of several sensitive information types already included by Microsoft, such as Credit Card Number or ABA Routing Number. See the sensitive information types inventory for a full list.
A new feature called Document Fingerprinting allows you to establish sensitive information types based on existing form documents you wish to keep secure. As an example, you might have patent templates, government forms, HIPPA forms that employees fill out, and so forth that can be used to generate a sensitive information type that is now protected through DLP and transport rules.
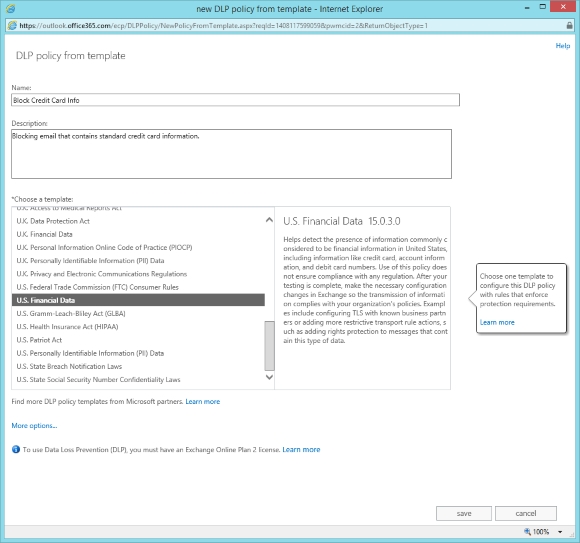
Creating a new Exchange Online DLP policy from a template.
(Image: J. Peter Bruzzese)
Of course, it is not just enough to identify sensitive information. You must also decide what to do when a policy for handling is violated. When a user tries to send an email that may contain sensitive information, you can alert them through DLP Policy Tips or take further action. Depending on your particular compliance policy, you can choose to have this Policy Tip provide a simple reminder, an outright block, or a block that can be overridden if the user indicates a false positive or provides a justification. You can even provide users with a link to your compliance policy for further reference. Customizing Policy Tips to your organization’s needs allows you to stay compliant without unnecessary interruptions to work flow.
As you begin to plan an implementation of Data Loss Prevention for your Exchange environment, you can create policies that are enabled in test mode only so that you can see how they work without affecting end users. Once you have activated policies, then you can use reporting and monitoring tools to see how your policies are invoked throughout the organization.
In future articles we’ll pursue how to work with DLP. But it’s important to understand the feature and value it brings to your organization first. Having the ability to prevent users from themselves is a good thing indeed.