Office 365 Takes Aim at Spoofers but Users See Warnings About Fraudulent Messages
[Update 19 March] Microsoft has partially rolled back the rigor of its anti-spoofing policy to reduce the number of messages marked as potentially fraudulent. This does not take away from the need for organizations to authenticate their outbound email stream so as to avoid problems in the future. All large email providers recommend that email senders are authenticated using one or more of DKIM, DMARC, and SPF. It’s up to you!
[Update 28 March] The formal bog announcing Microsoft’s anti-spoofing initiative is now online. It would have been nice had they communicated first before firing the gun…
The Spam War
Email vendors are in a state of constant warfare with hackers, attackers, spammers, spoofers, and generally anyone who wants to use email as a threat vector. This isn’t new, and we have ups and downs all the time as each side seeks to gain an advantage over the other.
I consider Office 365 to offer good protection against the bad guys through the combination of Exchange Online Protection (EOP) and, if you can afford it, Advanced Threat Protection (ATP). I’ve seen evidence of the commitment they have to eradicating bad stuff from email flowing into Office 365, a task that is surely the modern-day equivalent of Hercules cleaning out the Augean stables.
Behind the scenes, Microsoft tweaks their toolset and algorithms on an ongoing basis to deflect new threat, suppress new spam, and quash new attacks with features like Dynamic Delivery for attachments.
New Anti-Phishing Policy
Recently, they have concentrated on extending defenses against phishing attacks. Last month, Microsoft rolled out a new ATP anti-phishing policy to protect named users and domains against impersonation. But behind the scenes, they have developed new capabilities to prevent spoofers using domains with poor sender authentication to fool Office 365 users with phishing attacks.
The Problem with Sender Authentication
The history and nature of email is founded on some fundamental protocols like SMTP. The great thing about SMTP is that it enables dial-tone email where anyone can send just about anyone else email if they use an SMTP server. The bad thing about SMTP is that it is easy to spoof. Domains can use features like DKIM, SPF, and DMARC to prove their identity to the work, but the sad fact is that many large organizations continue to run email services that do not use sender authentication.
Microsoft Puts Heat on Poor Sender Authentication
Microsoft is now turning the screw on these services with a mixture of intelligence and force. The intelligence comes from observation of mail flow into Office 365 for millions of email domains to learn the usual send pattern for each domain. If anomalous send behavior (like emails coming from a previously unknown server in a different part of the world), a new anti-spoofing filter kicks in to stamp messages with embedded text to inform the recipient that the sender failed Microsoft’s fraud detection checks (Figure 1).
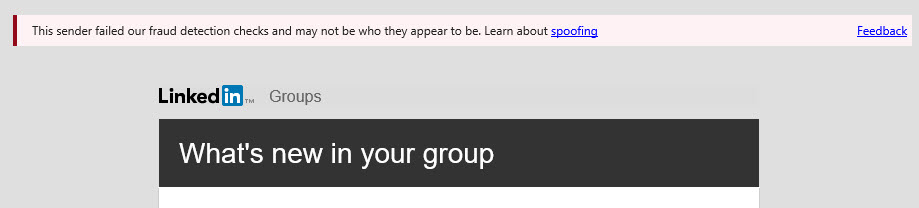
More information about why messages get “the sender failed our fraud detection checks” safety tip is available in Terry Zink’s very informative blog. And here’s some more reading about other safety tips inserted by EOP.
Making users aware of threat is good. The offending domains can easily stop Office 365 labelling their email as possibly fraudulent by configuring SPF, DMARC, or DKIM for their domain (see Terry’s blog for details). And in some cases, Microsoft is tweaking their filters to make sure that the kind of email sent by LinkedIn.com in Figure 1 is not caught in the net.
The Downside – Poor Communications
What’s bad here is that Microsoft forgot to tell anyone that they were going to enable the new anti-spoofing filter for ATP customers. I’ve noted a few messages arriving into my mailbox marked as possibly fraudulent and didn’t think too much about them because I have been playing with the new ATP anti-phishing filter, but the root cause is the new anti-spoofing filter that is enabled by default.
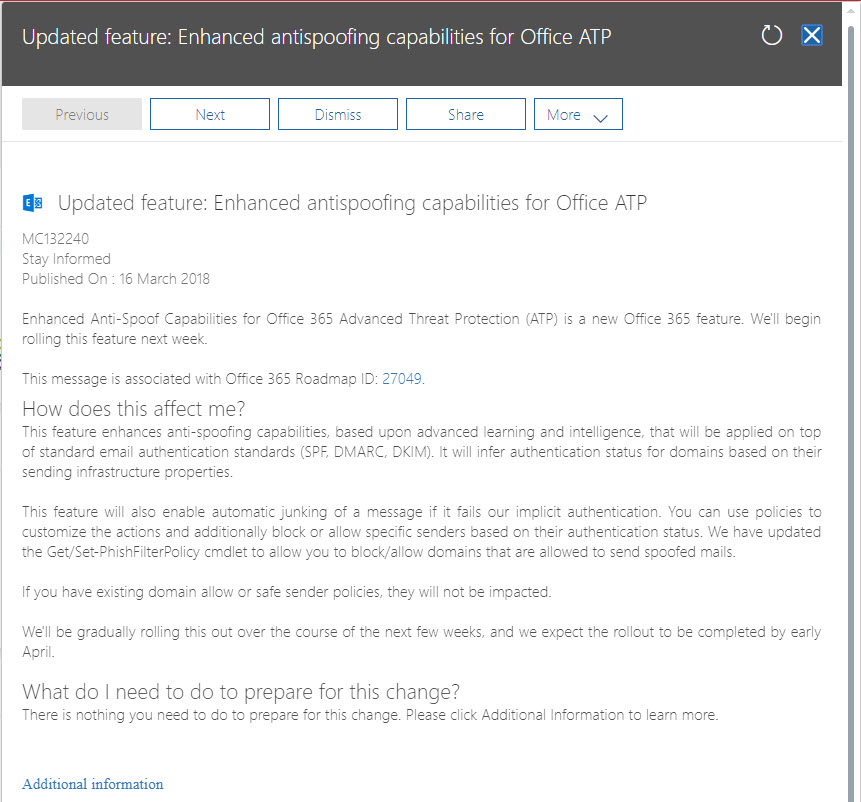
However, other recipients were not as sanguine, and many Office 365 tenants who use ATP reported a surge of marked messages flooding into user mailboxes. The “advanced learning and intelligence” claimed in the Office 365 Message Center update posted long after Microsoft introduced the new checks (Figure 2) clearly failed to deal with the many variations of email floating around the internet that do not have sender authentication.
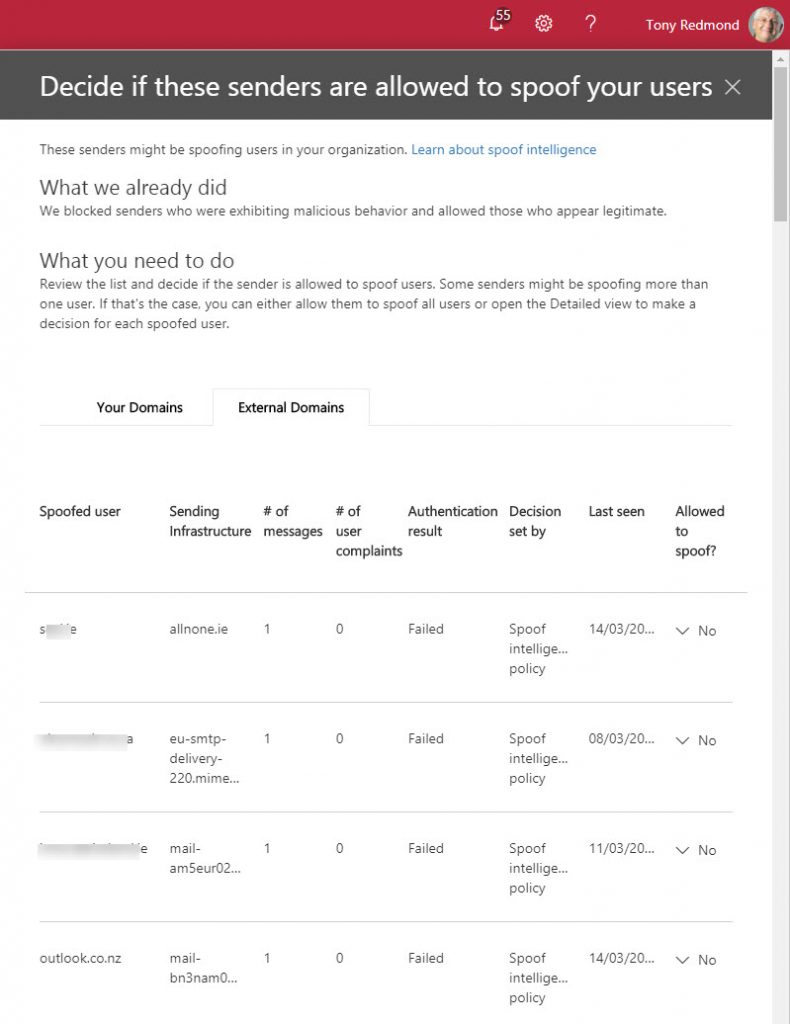
Checking for Potential Spoofs
If you have ATP for your Office 365 tenant, you can see details of senders flagged as potential problems through the Threat Management section of the Security and Compliance Center. Select Anti-spam and then scroll down to the Spoof Intelligence section (read this support article first). Click the Review new senders link. Figure 3 shows some data from my tenant.
Good Motives, Bad Planning
Microsoft’s motives were good. They wanted to deflect anti-phishing attacks that cause real pain and economic impact on their customers. The decision to enable the new filter was made with the best possible intention. However, because Microsoft did not give tenants a heads-up about their plans, administrators were not able to tell users that they might see messages from previously trusted senders now being marked as fraudulent. The result is confused end users and help desks who don’t know how to respond to user questions, which is always bad.
We’ve been down this path before when Microsoft launches new features into Office 365 without notice. The best (or worse) example is when Azure Active Directory introduced a new sign-on experience without warning anyone last August. Again, a good change in the long term, but horribly executed. Such poor communication and planning makes customers wonder about the ability of Microsoft to manage change within Office 365.
The Campaign for Sender Authentication Continues
The background tweaking and whitelisting of domains and mailing lists should soon bring the flood of marked messages back down to manageable levels. Eventually, once the domains who don’t use sender authentication get the idea that they should, the problem might go away. In the interim, read this support article to learn more about Microsoft Spoof Intelligence.
Follow Tony on Twitter @12Knocksinna.
Want to know more about how to manage Office 365? Find what you need to know in “Office 365 for IT Pros”, the most comprehensive eBook covering all aspects of Office 365. Available in PDF and EPUB formats (suitable for iBooks) or for Amazon Kindle.