Microsoft’s November Patch Tuesday Updates Fix 69 Windows Flaws

Microsoft has released yesterday the November 2022 Patch Tuesday for all supported versions of Windows 11 and Windows 10, including the freshly-released versions 22H2 of the two operating systems. This month, Microsoft fixed a total of 69 Windows vulnerabilities, with six of them already being exploited by attackers.
On the quality and experience updates front, Windows 11 version 22H2 is getting new tabs for File Explorer tabs as well as minor improvements for the taskbar. This is the first “Moment” update for Windows 11 following the release of the 2022 Update in October.
69 vulnerabilities fixed in the November 2022 Patch Tuesday updates
Among the 69 Windows vulnerabilities Microsoft fixed this month, 11 are rated “Critical” and 3 of them are already being exploited by attackers. Three more vulnerabilities rated “Important” are also being exploited in the wild, and you can find more details about all of them below:
- CVE-2022-41091: This Windows Mark of the Web Security Feature Bypass public vulnerability allows attackers using a malicious file to bypass Mark of the Web (MOTW) defenses,resulting in a limited loss of integrity and availability of security features such as Protected View in Microsoft Office.
- CVE-2022-41040: This Microsoft Exchange Server Elevation of Privilege vulnerability allows authenticated attackers to run PowerShell commands on the system.
- CVE-2022-41082: This Microsoft Exchange Server Remote Code Execution vulnerability allows authenticated attackers to trigger malicious code in the context of the server’s account through a network call.
- CVE-2022-41128: This Windows Scripting Languages Remote Code Execution vulnerability affects the JScript9 scripting language. It can only be exploited by attackers by convincing users to visit a specially crafted server share or website.
- CVE-2022-41125: Windows CNG Key Isolation Service Elevation of Privilege vulnerability can allow attackers to gain system privileges.
- CVE-2022-41073: This Windows Print Spooler Elevation of Privilege vulnerability can also allow attackers to gain system privileges.
You can find the full list of CVEs released by Microsoft with the November 2022 Patch Tuesday updates below:
| Product | Impact | Max Severity | Article | Details |
| Windows Server 2012 R2 (Server Core installation) | Remote Code Execution | Critical | 5018474 | CVE-2022-22035 |
| Windows Server 2012 R2 (Server Core installation) | Remote Code Execution | Critical | 5018476 | CVE-2022-22035 |
| Windows Server 2012 R2 | Remote Code Execution | Critical | 5018474 | CVE-2022-22035 |
| Windows Server 2012 R2 | Remote Code Execution | Critical | 5018476 | CVE-2022-22035 |
| Windows Server 2012 (Server Core installation) | Remote Code Execution | Critical | 5018457 | CVE-2022-22035 |
| Windows Server 2012 (Server Core installation) | Remote Code Execution | Critical | 5018478 | CVE-2022-22035 |
| Windows Server 2016 | Remote Code Execution | Critical | 5018411 | CVE-2022-30198 |
| Windows 10 Version 1607 for 32-bit Systems | Remote Code Execution | Critical | 5018411 | CVE-2022-22035 |
| Windows 10 for 32-bit Systems | Information Disclosure | Important | 5018425 | CVE-2022-38043 |
| Windows 10 Version 21H2 for 32-bit Systems | Remote Code Execution | Critical | 5018410 | CVE-2022-30198 |
| Windows 11 for ARM64-based Systems | Remote Code Execution | Critical | 5018418 | CVE-2022-22035 |
| Windows 11 for x64-based Systems | Remote Code Execution | Critical | 5018418 | CVE-2022-22035 |
| Windows RT 8.1 | Denial of Service | Important | 5018474 | CVE-2022-38041 |
| Windows 10 Version 21H1 for 32-bit Systems | Remote Code Execution | Critical | 5018410 | CVE-2022-22035 |
| Windows 10 Version 21H1 for ARM64-based Systems | Remote Code Execution | Critical | 5018410 | CVE-2022-22035 |
| Windows 10 Version 20H2 for ARM64-based Systems | Information Disclosure | Important | 5018410 | CVE-2022-38043 |
| Windows 10 Version 20H2 for 32-bit Systems | Information Disclosure | Important | 5018410 | CVE-2022-38043 |
| Windows Server 2022 (Server Core installation) | Remote Code Execution | Critical | 5018421 | CVE-2022-30198 |
| Windows 10 Version 1809 for 32-bit Systems | Denial of Service | Important | 5018419 | CVE-2022-38041 |
| Windows Server 2012 | Elevation of Privilege | Important | 5018457 | CVE-2022-37986 |
| Windows Server 2012 | Elevation of Privilege | Important | 5018478 | CVE-2022-37986 |
| Windows 10 Version 1809 for x64-based Systems | Remote Code Execution | Important | 5018419 | CVE-2022-38040 |
| Windows Server 2016 (Server Core installation) | Spoofing | Important | 5018411 | CVE-2022-35770 |
| Windows 10 Version 1809 for ARM64-based Systems | Elevation of Privilege | Important | 5018419 | CVE-2022-37987 |
| Windows 10 Version 21H2 for x64-based Systems | Elevation of Privilege | Important | 5018410 | CVE-2022-37997 |
| Windows 10 Version 21H2 for ARM64-based Systems | Elevation of Privilege | Important | 5018410 | CVE-2022-37997 |
| Windows 10 Version 20H2 for x64-based Systems | Elevation of Privilege | Important | 5018410 | CVE-2022-37997 |
| Windows Server 2022 | Elevation of Privilege | Important | 5018421 | CVE-2022-37997 |
| Windows 8.1 for 32-bit systems | Elevation of Privilege | Important | 5018474 | CVE-2022-37987 |
| Windows 8.1 for 32-bit systems | Elevation of Privilege | Important | 5018476 | CVE-2022-37987 |
| Windows Server 2019 | Elevation of Privilege | Important | 5018419 | CVE-2022-38045 |
| Windows Server 2012 R2 (Server Core installation) | Spoofing | Critical | 5016681 | CVE-2022-34689 |
| Windows Server 2012 R2 (Server Core installation) | Spoofing | Critical | 5016683 | CVE-2022-34689 |
| Windows Server 2012 R2 | Spoofing | Critical | 5016681 | CVE-2022-34689 |
| Windows Server 2012 R2 | Spoofing | Critical | 5016683 | CVE-2022-34689 |
| Windows Server 2012 (Server Core installation) | Spoofing | Critical | 5016672 | CVE-2022-34689 |
| Windows Server 2012 (Server Core installation) | Spoofing | Critical | 5016684 | CVE-2022-34689 |
| Windows Server 2012 | Spoofing | Critical | 5016672 | CVE-2022-34689 |
| Windows Server 2012 | Spoofing | Critical | 5016684 | CVE-2022-34689 |
| Windows 10 for 32-bit Systems | Spoofing | Critical | 5016639 | CVE-2022-34689 |
| Windows Server 2019 | Spoofing | Critical | 5016623 | CVE-2022-34689 |
| Windows 10 Version 1809 for ARM64-based Systems | Spoofing | Critical | 5016623 | CVE-2022-34689 |
| Windows 10 Version 1809 for x64-based Systems | Spoofing | Critical | 5016623 | CVE-2022-34689 |
| Windows Server 2019 (Server Core installation) | Elevation of Privilege | Critical | 5018419 | CVE-2022-37976 |
| Windows 8.1 for x64-based systems | Denial of Service | Important | 5018474 | CVE-2022-38041 |
| Windows 8.1 for x64-based systems | Denial of Service | Important | 5018476 | CVE-2022-38041 |
| Windows 10 Version 1607 for x64-based Systems | Elevation of Privilege | Important | 5018411 | CVE-2022-38028 |
| Windows 10 for x64-based Systems | Elevation of Privilege | Important | 5018425 | CVE-2022-38028 |
| Windows 10 Version 1809 for 32-bit Systems | Spoofing | Critical | 5016623 | CVE-2022-34689 |
| Windows 10 Version 21H1 for x64-based Systems | Remote Code Execution | Critical | 5018410 | CVE-2022-33634 |
| Windows RT 8.1 | Spoofing | Critical | 5016681 | CVE-2022-34689 |
| Windows 8.1 for x64-based systems | Spoofing | Critical | 5016681 | CVE-2022-34689 |
| Windows 8.1 for x64-based systems | Spoofing | Critical | 5016683 | CVE-2022-34689 |
| Windows 8.1 for 32-bit systems | Spoofing | Critical | 5016681 | CVE-2022-34689 |
| Windows 8.1 for 32-bit systems | Spoofing | Critical | 5016683 | CVE-2022-34689 |
| Windows Server 2016 (Server Core installation) | Spoofing | Critical | 5016622 | CVE-2022-34689 |
| Windows Server 2016 | Spoofing | Critical | 5016622 | CVE-2022-34689 |
| Windows 10 Version 1607 for x64-based Systems | Spoofing | Critical | 5016622 | CVE-2022-34689 |
| Windows 10 Version 1607 for 32-bit Systems | Spoofing | Critical | 5016622 | CVE-2022-34689 |
| Windows 10 for x64-based Systems | Spoofing | Critical | 5016639 | CVE-2022-34689 |
| Windows 10 Version 21H2 for x64-based Systems | Spoofing | Critical | 5016616 | CVE-2022-34689 |
| Windows 10 Version 21H2 for ARM64-based Systems | Spoofing | Critical | 5016616 | CVE-2022-34689 |
| Windows 10 Version 21H2 for 32-bit Systems | Spoofing | Critical | 5016616 | CVE-2022-34689 |
| Windows 11 for ARM64-based Systems | Spoofing | Critical | 5016629 | CVE-2022-34689 |
| Windows 11 for x64-based Systems | Spoofing | Critical | 5016629 | CVE-2022-34689 |
| Windows 10 Version 20H2 for ARM64-based Systems | Spoofing | Critical | 5016616 | CVE-2022-34689 |
| Windows 10 Version 20H2 for 32-bit Systems | Spoofing | Critical | 5016616 | CVE-2022-34689 |
| Windows 10 Version 20H2 for x64-based Systems | Spoofing | Critical | 5016616 | CVE-2022-34689 |
| Windows Server 2022 (Server Core installation) | Spoofing | Critical | 5016627 | CVE-2022-34689 |
| Windows Server 2022 | Spoofing | Critical | 5016627 | CVE-2022-34689 |
| Windows 10 Version 21H1 for 32-bit Systems | Spoofing | Critical | 5016616 | CVE-2022-34689 |
| Windows 10 Version 21H1 for ARM64-based Systems | Spoofing | Critical | 5016616 | CVE-2022-34689 |
| Windows 10 Version 21H1 for x64-based Systems | Spoofing | Critical | 5016616 | CVE-2022-34689 |
| Windows Server 2019 (Server Core installation) | Spoofing | Critical | 5016623 | CVE-2022-34689 |
Quality and experience updates
On Windows 11 version 22H2, the KB501998 patch brings several UI and UX changes including File Explorer Tabs. This has been a top-requested feature since Microsoft briefly tested a similar “Windows Sets” feature on Windows 10 many years ago.
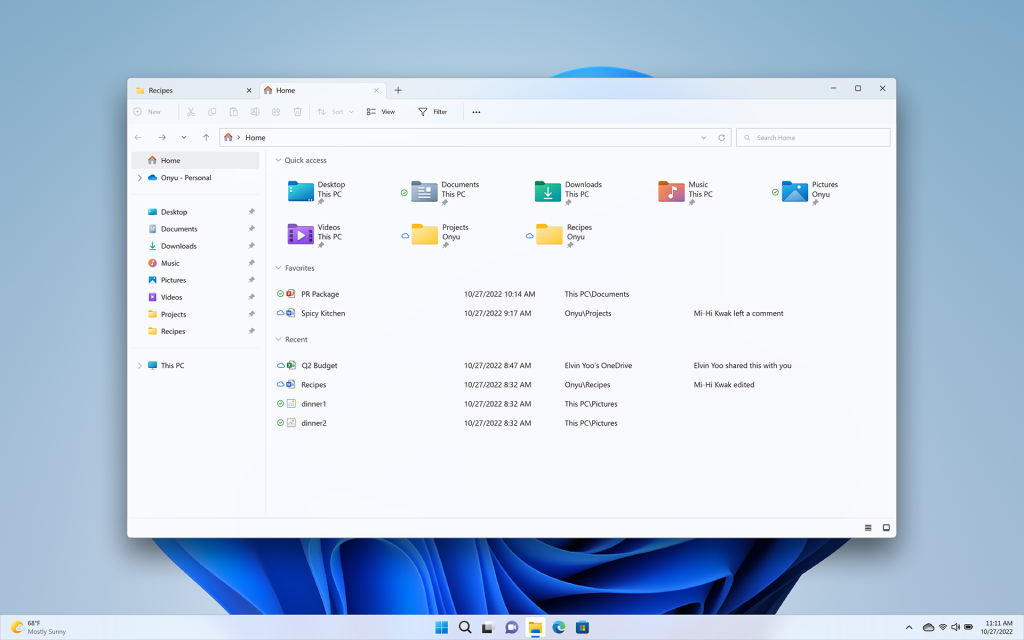
The Windows 11 taskbar is also getting several improvements this month: It’s now possible to access Task Manager from the context menu when you right-click the taskbar, and a new taskbar overflow menu also lets you see all the pinned apps that couldn’t fit in your taskbar. Microsoft has also started testing different visual treatments for the Search on the taskbar, and some users may now see different versions of the search button.
Microsoft has also updated the Settings app this month. The page displaying Microsoft Account settings now lets users manage their OneDrive subscription and see storage alerts. The company is also testing visual enhancements for the backup experience when using a Microsoft account on Windows 11.
The video below provides more details about all the quality and experiences updates coming to Windows 11 version 22H2 this month:
For Windows 11 users still running the version 21H2 of the OS, the KB5019961 patch also brings back the shortcut to Task Manager when you right-click the taskbar. Additionally, this update should improve Windows search results and performance.
The KB5019959 patch is also available for Windows 10 versions 20H2, 21H1, 21H2, and 22H2. Microsoft only detailed security updates in this patch and there are no new features. If you’re wondering, the company still isn’t sharing details about the “scoped set of new features” included in the 22H2 update for Windows 10.
Windows Update testing and best practices
Organizations looking to deploy this month’s patches should conduct thorough testing before deploying them widely on production systems. That said, applying the patches widely shouldn’t be delayed longer than necessary as hackers start to work out how to weaponize newly reported vulnerabilities.
A best practice is to make sure you have backed up systems before applying updates. Every month, users experience issues with Windows updates that lead to systems not booting, application and hardware compatibility issues, or even data loss in extreme cases.
There are backup tools built into Windows and Windows Server that you can use to restore systems in the event a patch causes a problem. The backup features in Windows can be used to restore an entire system, or files and folders on a granular basis.
If you have any problems with this month’s patches, please let us know in the comments below. Other readers might be able to share their experiences in how to roll back problematic updates or mitigate issues caused by patches that are important to have in place.



