With the end of support for Windows XP fast approaching (April 14, 2014), it’s time to consider migrating to a modern desktop operating system like Windows 8. As I outlined in my previous post here on the Petri IT Knowledgebase, there are some compelling security reasons to move away from Windows XP. When support ends for Windows XP, Microsoft will no longer produce security updates for XP. However, there will continue to be vulnerabilities, meaning that Windows XP systems still in use after the support deadline passes are likely to have perpetual zero-day vulnerabilities. I also describe some of the new security features in Windows 8. With the forthcoming release of Windows 8.1, Microsoft has added additional security features that will be of great benefit to consumers and enterprises alike. Today I’ll go over some of the important new security features in Windows 8.1.
With Windows 8, Microsoft invested heavily in making the operating system resistant to malware. In Windows 8.1, they have placed a heavy emphasis on modern access control and have focused on things like strong identification and authentication, platform trustworthiness, and consumer device management, just to name a few.
Windows 8.1 Security Features
Biometrics
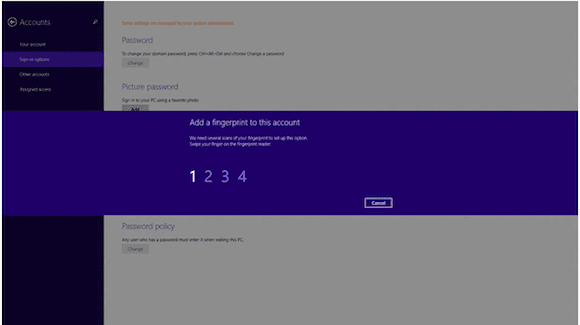
Strong authentication is essential for the security of any system, and to that end Microsoft is determined to provide a first-class biometrics experience in Windows 8.1, including a biometric sign-in option for all Windows experiences, including initial logon, remote access, and all remaining authentication prompts. Microsoft has also enabled a “touch to buy” experience for their online services such as the Windows Store, Xbox Music, and Xbox live. In-app purchases can be authenticated using a biometric device as well. In the past, biometric devices such as fingerprint scanners often required the users to swipe their finger across the reader, which typically resulted in a poor user experience by having to swipe numerous times to initially enroll, and subsequently authenticate. To remedy this situation, Microsoft has been working closely with OEM hardware partners to ensure that the latest capacitive fingerprint readers are used, which work simply by touching the sensor. The end result is near instantaneous authentication, which ultimately provides a much better user experience and leads to increased adoption of the technology.
An added benefit to capacitive fingerprint readers is that they have the ability to detect liveness, which can mitigate most fingerprint spoofing attacks. It’s important to understand that biometrics in Windows 8.1 are built on top of passwords, so passwords have not been eliminated. However, using biometrics can allow the use of much longer and more complex passwords than would otherwise be feasible without biometrics.
(Image via Technet)
Multifactor Authentication
Windows 8 included support for virtual smart cards, which are certificates that are stored on the computer’s Trusted Platform Module (TPM). Virtual smart cards provide valuable two-factor authentication today, and in Windows 8.1 virtual smart cards can now be provisioned to non-domain joined devices. This will become a key driver for the adoption and management of consumer devices in the enterprise, as many organizations are struggling with the challenges of embracing Bring Your Own Device (BYOD) while at the same time protecting corporate assets and providing fine-grained access control for authorized users.
Trusted Platform Module (TPM) Support
Although not necessarily a security feature of the Windows operating system itself, TPM is an essential component for many of the security features provided by Windows, including virtual smart card, BitLocker, provable PC health, and more. TPM really is the key to the modern access control story, and with a heavy reliance on this hardware component, Microsoft will be making TPM a requirement for Windows certification in the future. Today, however, there are chipsets that now support Platform Trust Technology (PTT), which provides a virtual TPM that can be leveraged by the operating system to provide essential security services.
Certificate Handling
Certificates are an important technology and are vital to providing the highest levels of confidentiality, integrity, and non-repudiation. The security of any solution that relies on digital certificates to establish trust and ensure privacy ultimately depends on the trustworthiness of those certificates. In Windows 8.1, Microsoft has taken steps to ensure that certificates are better protected on the client by now encrypting them on the device. This feature is designed to prevent certificate theft by ensuring that certificates aren’t useable if an attempt is made to export them from the device after they have been issued.
If you think that simply marking a certificate as non-exportable prevents this attack, you are quite mistaken. There are a number of tools available today that have the capability to export certificates that are marked non-exportable. To further ensure the validity of certificates installed on the endpoint, Windows 8.1 now includes TPM key attestation capabilities, which allows for the remote verification that a certificate was provisioned securely and properly encrypted on the endpoint. As an additional layer of protection for systems that rely on digital certificates, Microsoft now has a cloud-based service that gathers detailed information about certificates in use on the public Internet. This telemetry data is closely monitored for signs of anomalous behavior that might be indicative of a certificate compromise. In the event a certificate appears not to be genuine, Microsoft will alert the owners of the domain in question so they can investigate and remediate if necessary.
Workplace Join
BYOD, the trend to use consumer devices to access corporate data and applications, presents a significant challenge for security administrators everywhere. Granting access to corporate resources to unknown and untrusted devices brings with it great risks. To mitigate these concerns and help administrators enable and embrace BYOD, Windows 8.1 now includes a feature called Workplace Join which allows consumer devices such as the Windows Surface RT, along with iPads and Android tablets, to be joined to the corporate domain. Through the process of device registration, the end users opts-in to having corporate security and data protection policies enabled on their device. In this scenario, personal and corporate data can co-exist without issue. If the user or an administrator decides to un-enroll the device, any corporate data on the device will be deleted while the user’s personal data is left intact.
Device Encryption
With Windows 8.1, Microsoft has now made device encryption available on all editions of Windows. Built on BitLocker technology, this feature is designed to ensure the protection of data on mobile devices and leverages Universal Extensible Firmware Interface (UEFI) and TPM technologies. Device encryption requires that the hardware not include any DMA-based high speed serial ports, as these ports make the retrieval of encryption keys from memory trivial.
Provable PC Health
To provide additional protection against rootkits, Windows 8.1 leverages a new cloud-based service that can provide remote attestation of system health and configuration. This is essential, as rootkits typically mask their presence and provide false information to the operating system and any protection mechanisms that initialize later in the boot process after the rootkit has been loaded. With this new feature, Windows 8.1 will collect system initialization data such as measured boot information, version and hash values for critical operating system files and kernel mode drivers, and action center status for which the cloud service will analyze remotely and compare the information to its database of known values. If an issue is detected, the service can notify and suggest a course of remediation, such as running Windows Offline Defender. In addition, if the service recognizes a potential compromise of identity-related information (e.g. a keystroke logger is detected), the user will be notified and asked to change their password.
Additional Improvements to Windows 8.1
In addition to the improvements in identification, authorization, and hardware trustworthiness, Windows 8.1 also includes enhancements to existing protection mechanisms like Windows Defender. In Windows 8.1, Windows Defender now includes network behavior monitoring, allowing for the detection of malware based on malicious software known patterns of behavior. Additional changes to the underlying operating system enable Windows Defender or third-party anti-malware solutions to now scan Internet Explorer ActiveX controls or other binary extensions to be scanned prior to execution, greatly improving the overall security of the web browser.
Although there’s been just a little more than a year since Windows 8 was released, you can see that Microsoft has made significant improvements in security with the Windows 8.1 release. Strong authentication with biometrics, multi-factor authentication with virtual smart cards, increased device and operating system trustworthiness, improved data protection for BYOD scenarios, and continuing improvements in malware resistance make Windows 8.1 the most secure Microsoft desktop operating system by far.