Is Exchange Online Threatened by Ransomware?

The question of whether ransomware could infect and encrypt an Exchange Online mailbox raised by Michael Van Horenbeeck is fair. Although no reports exist of such an infection, the tools are there and, no doubt, someone is willing to try such an attack.
Vendors of cloud backup solutions like to raise this point with potential customers. They argue that Microsoft’s strategy of using Native Data Protection to avoid the need for backups of Exchange Online mailboxes is insufficient in a world where deliberate acts of malfeasance, such as ransomware attacks, are well known.
Files Restore
The existence of ransomware is one of the reasons why Microsoft introduced the Files Restore feature for OneDrive and SharePoint. This feature depends on versions of documents being available to allow recovery to a selected point in time. The versions of Word, Excel, and PowerPoint used with Office 365 support automatic versioning (“AutoSave”) to ensure that versions are available for recovery.
Attacking Exchange Online
Exchange is not SharePoint, or so I am told (the two products once shared the same database engine). A ransomware attack against a OneDrive for Business account or SharePoint document library could potentially lead to infection across an entire tenant, depending on factors such as the type of attack, how it spreads, and the sharing behavior of users. Advanced Threat Protection (ATP) for SharePoint can detect and suppress sharing of infected files, but perhaps only after some harm is done. However, assuming good versions of documents exist, the Files Restore feature allows users to recover their own files. If not, Microsoft can recover complete site collections from backup. A restore overwrites everything in the site collection, so it’s not a great solution.
An attack against Exchange could spread even faster if someone was to email malware to large segments of the organization. Exchange’s anti-malware defenses are likely to catch and disinfect most attempts to distribute bogus applications via email in real time. The kind of attack on Office 365 described in 2018 by Kevin Mitnick features an app delivered to an inbox. At this point you’d hope that most people are wise enough to realize that unknown applications that appear in the inbox should be treated with the utmost suspicion. Alas, this user is (insert favorite descriptor) silly enough to overlook the obvious clues (Figure 1) that the application shouldn’t be trusted and go ahead to allow it access to their mailbox.
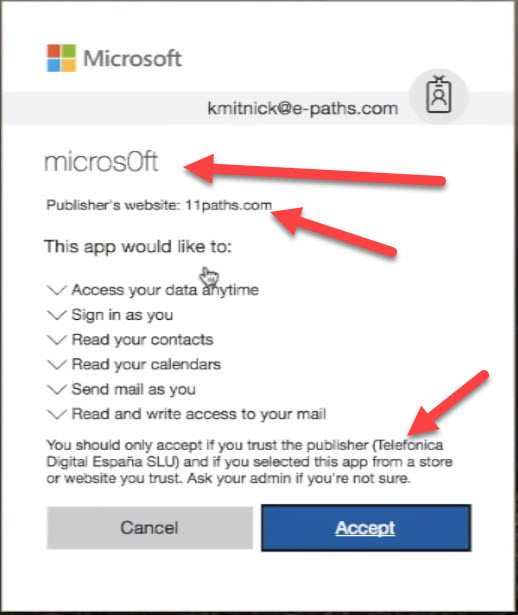
Arriving by email is a natural attack vector against Exchange Online. It’s possible that an application could gain access another way, like a direct attack against the user account (a good reason to use MFA everywhere) or malware shared in a document,
Once an application has access, the malware can encrypt messages as quickly as it can fetch items from the user’s mailbox. The app worked reasonably quickly with what seemed to be a set of draft messages in the demo mailbox; it’s entirely possible that it might not do quite so well with a large mailbox containing hundreds of thousands of items. In any case, the damage was done, and the encrypted items required a Bitcoin payment before they can be decrypted.
Lagged Database Doesn’t Help
The form of Native Data Protection used by Exchange Online includes a lagged copy of each mailbox database. It is technically possible for Microsoft to restore a mailbox from the lagged copy any time within seven days of the current time. A tenant administrator can’t do this because they have no way to mount the lagged copy and recover the data to the target mailbox like they can with an on-premises database. For their own good reasons, Microsoft doesn’t offer such a recovery service, possibly because they have not built an automated process to recover a mailbox from the lagged database. Automation is a sine que non for high-touch operations within Office 365.
Do Third-Party Backups Help?
So, is a third-party cloud backup the only viable solution if your tenant was unlucky enough to be attacked, the malware gets through to a mailbox, and the owner of the mailbox unwise enough to allow the malware free rein over their data? You’d have to be very unlucky for all the pieces to allow a successful attack to click into place, but it could.
Backup vendors can recover a mailbox to a point in time before the attack happens. If a vendor cannot, then you should lose any interest you might have in their services. But even if a recovery is possible, it will take time. In fact, given the swelling size of many Exchange Online mailboxes these days, it’s an interesting exercise to see just how long a recovery operation takes.
But as I have advocated in the past, before rushing to invest in an add-on cloud backup service to guard against a threat that is of marginal probability, think about what you could do with out-of-the-box functionality that you’re already paying for.
Recovery Through Held Items
For example, mailboxes on litigation hold are protected because any change to a mailbox item caused by malware encrypting the content or an item’s properties will force Exchange to capture a copy of the item before the change (copy on write). The same is done for holds placed on mailboxes by Office 365 eDiscovery cases.
In effect, the copies in the Recoverable Items structure are a get out of jail card because you can run a content search to find all the items in the mailbox and export the results to one or more PSTs. The PSTs will include the bad (encrypted) items, but also include the good (pre-encryption) copies.
Recovery is a matter of deleting the bad items from the online mailbox and copying the good items back. Remember to take the mailbox off hold before deleting the bad items from it as you don’t want Exchange to copy those items. This is not a fast way to restore a mailbox to good health. It’s also a manual, tiresome process that might involve using Outlook desktop to move tens of thousands of items from PST to mailbox.
Litigation hold is not designed to protect against ransomware and content search exports aren’t there to recover infected mailboxes. But the process works and uses tools built into Exchange. Nothing else is needed to restore the infected mailbox.
Protecting Items with Office 365 Encryption
Another thing you can do is use Office 365 Message Encryption (OME) and Office 365 Sensitivity Labels to protect important messages. All Office 365 tenants with E3 licenses (or above) can use inbuilt encryption for email, and if a message is already encrypted, I doubt that malware could update its content unless the app can gain superuser permission. Although content (including attachments) is safe, malware will be able to interfere with a message’s properties like its subject because this data is not encrypted.
Again, this is functionality readily available to Exchange Online users, if tenants take the time to educate people about how to use encryption effectively.
Possibility Exists, but Likelihood is Small
Don’t get me wrong. I do not underestimate threat and I do not underestimate the fearsome intellect that some attackers exert when coming up with new and innovative ways to penetrate systems to steal or compromise data. It is entirely possible that someone could build and execute a ransomware attack against Exchange Online. But the likelihood of success is very small, unless your anti-malware defenses are weak, and users like to dabble with the dark art of trusting unknown applications.
Given that Microsoft has the Files Restore feature for OneDrive and SharePoint, it’s reasonable to ask if they could do the same for Exchange. The lagged database copy is the obvious place to look because it will work for every mailbox, including those not on hold. Maybe Microsoft will do something in this area in the future. Until then:
- Use MFA to protect user accounts to reduce the chance that a direct attack against Office 365 accounts will succeed.
- If you’re concerned about the possibility of ransomware attacks against Exchange Online mailboxes, consider placing sensitive mailboxes on litigation hold. Many sensitive mailboxes are already on hold for one reason or another, so this isn’t a big step.
- Consider using Office 365 Message Encryption and Office 365 Sensitivity Labels to protect important email. Using these features requires user education. Encryption is not something to launch on a whim.
- Educate users to treat every application that asks for access to their mailbox with great suspicion. You never know when malware will penetrate your anti-malware defenses.


