Throughout 2014, news of electronic data theft was rarely out of the mainstream headlines in the United States. Target, Home Depot, Kmart, Sony, and and more made headlines. The nature of attacks and attackers has changed. Gone, mostly, are the days of some teenager stretching their hacker wings from their parent’s basement, and now we’re in the days of well-funded professional thieves, government-sponsored espionage, and hacktivism.
A group called 27001 Academy posted an infographic not long ago that summarizes the nature and quantity of data breaches in the United States throughout last year. The United States is a small percentage of the world’s population, but we can probably use the presented statistics as a sample for what happened in the rest of the world.
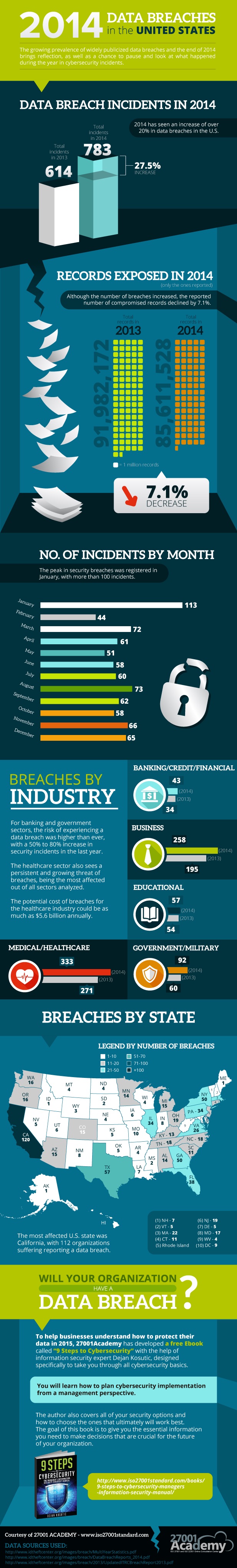
Year on Year Growth
2014 was a good year for digital thieves. According to 27001 Academy, there was a 27.5% increase in data breaches in the United States, up from 616 incidents to 783. We cannot expect these figures to start a permanent slide for quite some time. There is just too much potential profit to be made by criminal organizations, and sadly in my opinion, some organizations are criminally negligent with updating and protecting their systems and applications.
On a positive note, the number of reported data breaches was down by 7.1% from 91,982,172 breached data records to 85,611,528. I don’t think we can jump for joy with this news. Control was lost over some 85 million individual data records, potentially affecting 85 million people in the USA and abroad.
There was a pretty uniform distribution attacks across 2014 with an average of 60.99 incidents per month with one exception; January had an 85% higher than normal rate of incidents. I am not aware of any reason for this spike; maybe it was a hangover from the Target breach in late 2013, which happened in November to December 2013 but made news in January 2014.
Affected Industries
There is good news for those working in education; the number of attacks only rose from 54 to 57. Government and military sites are obvious targets for espionage and hacktivism, or maybe it is a coincidence that the Chinese Shenyang J-31 stealth fighter bears a striking resemblance to the American-made F-35.
The medical industry saw an increase from 271 to 333 incidents. Why would anyone want my medical records? I doubt they want to see anyone’s dental records or prescriptions, but social security numbers and payment details are usually stored in medical databases and have a significant value. It is estimated that the cost to the US healthcare industry might be as much as $5.6 billion.
Banks, those companies that often insist on using Java apps to access their services, have also seen a 26% rise in incidents since 2013.
The business category, which is just ordinary organizations, saw a significant rise from 195 to 258 attacks. Most of us don’t think that we have state secrets to hide. But obviously we have information of value. Think about it; how do your employers take payments and bank profits? But there are less obvious prizes too, like gateways into partner companies. It is rumored that an attack on RSA led to 70+ such attacks a few years ago.
Security is a Moving Target
The old days of install antivirus, approve your updates, and install a firewall are long since past. Security is a full-time profession. Zero-day attacks are crippling businesses. Legacy active scanning anti-malware cannot keep up with the escalating rate of threat releases. Organizations need to implement real, layered, multi-vendor and multi-dimensional defenses, accompanied by genuine director-level support, employee education, and enforcement.
Actually, that advice was valid years ago. In the real world, we know these sorts of polices are often announced but don’t really happen. Attacks are growing in frequency, targeting small-to-medium businesses, government, and large enterprises. The data contained in this infographic provide the evidence that we need to learn how to continually evolve and improve our defenses against this agile and very motivated attackers.