How to Set Up Passwordless Sign-in Using the Microsoft Authenticator App for Microsoft 365
As the identity management platform used by Microsoft 365, Azure Active Directory (AD) is used to control and manage user access to Microsoft 365 services and apps. When passwordless sign-in is enabled in Azure AD, instead of entering a password users can confirm their identity using the Microsoft Authenticator app, a FIDO2 security key, or by SMS message.
In this article, I will show you how to let users securely log in to Microsoft 365 using the Microsoft Authenticator app instead of a password.
Passwords are a security risk and difficult to manage
Around 80 percent of successful attacks originate from compromised passwords. IT departments spend a lot of time managing passwords and recovering from security incidents where password exposure was the root cause. Multifactor authentication (MFA) is very effective at protecting passwords but it has a low adoption rate.
Microsoft is championing passwordless sign-in because it is more convenient for users and it provides a higher level of security than passwords. For additional information on passwordless sign-in and why passwords are a security risk, check out Understanding Windows 10 and Microsoft 365 Passwordless Sign-In on Petri.
Pre-requisites for passwordless sign-in
The first requirement for passwordless sign-in in Microsoft 365 is that the ‘combined registration’ experience must be enabled in Azure AD. Combined registration brings together the registration experience for Azure MFA and self-service password reset. Beginning August 15th 2020, all new Azure AD tenants are automatically opted in for combined registration.
If you have an Azure AD tenant that was provisioned before August 15th 2020, you’ll need to enable combined registration manually.
Enable combined registration in Azure AD
You can enable combined registration by logging in to Azure AD using a global administrator account.
- Log in to Azure AD here.
- Click Azure Active Directory under Favorites on the left of the portal window.
- In the Azure AD pane, scroll down the list of options on the left, and click Security under Manage.
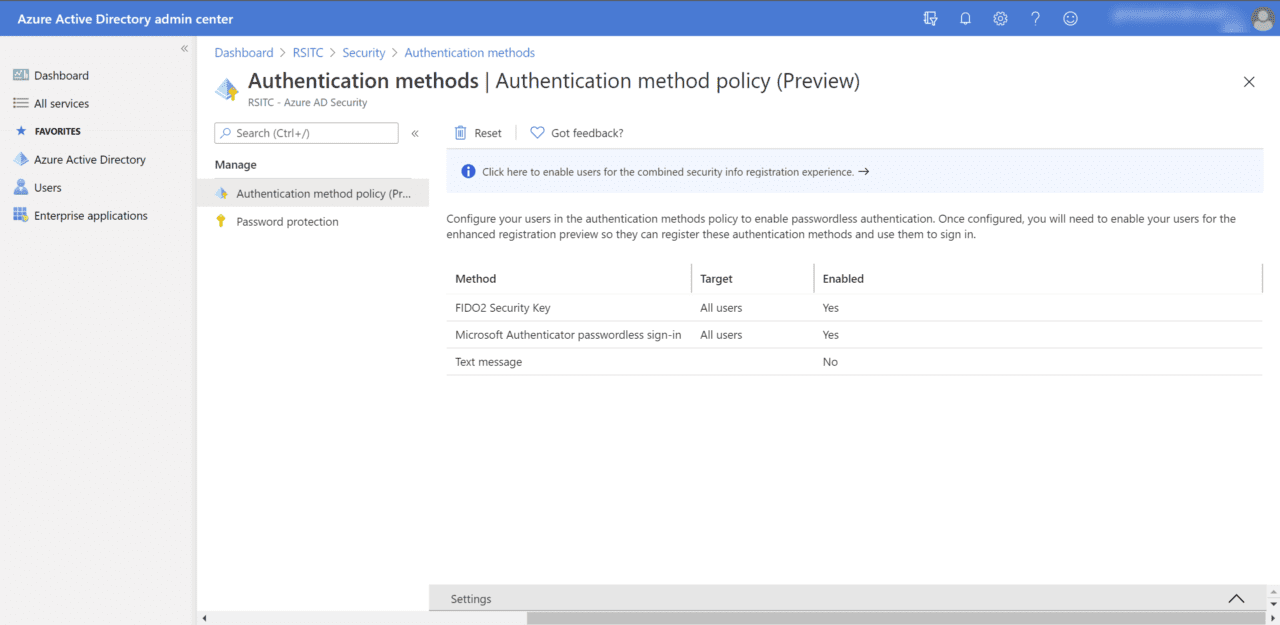
- In the Security pane, click Authentication methods below Manage in the list of options on the left.
- On the right of the Authentication methods pane, click ‘Click here to enable users for the combined security info registration experience’.
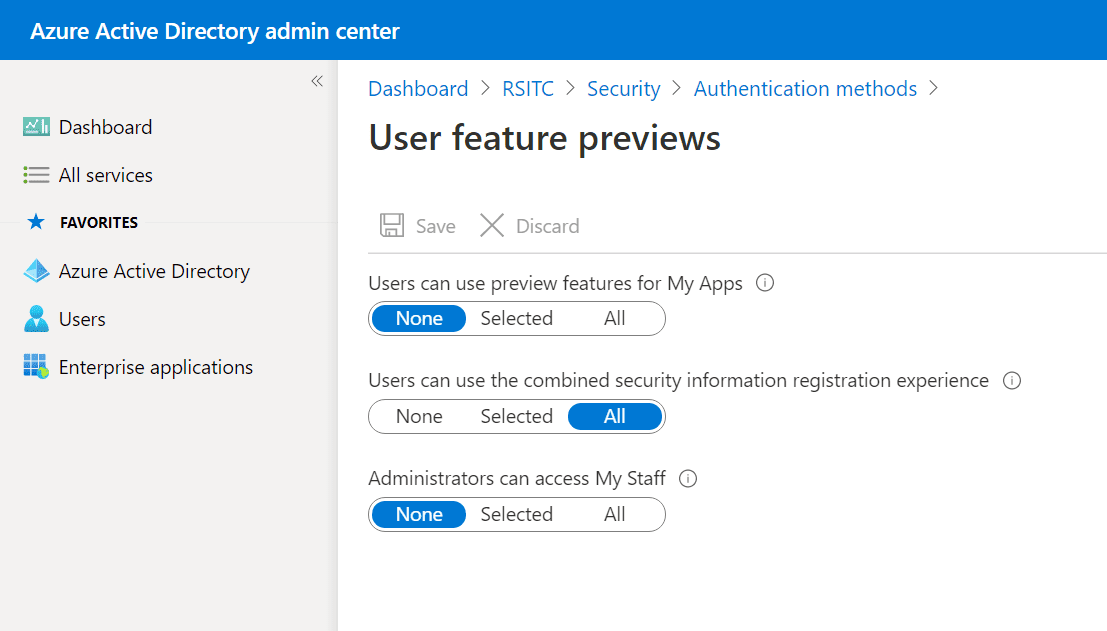
- In the User feature previews pane, set Users can use the combined security information registration experience to All and then click Save.
Optionally, you can click Selected and then pick a group of users instead of enabling combined registration for all users in the directory.
Users must self-register Microsoft Authenticator to use passwordless sign-in
Users must register the Microsoft Authenticator app as an authentication method before they can use passwordless sign-in. If users have already registered Microsoft Authenticator for use with multifactor authenticator, they won’t need to reregister the app for use with passwordless sign-in.
You can enable multifactor authentication for users, either individually or in bulk, in the Microsoft 365 admin portal. For detailed instructions on how to set up multifactor authentication, see Enable Multi-Factor Authentication for Office 365 Users on Petri. Regardless of whether users are setup for passwordless sign-in, multifactor authentication should still be enabled and enforced to protect passwords.
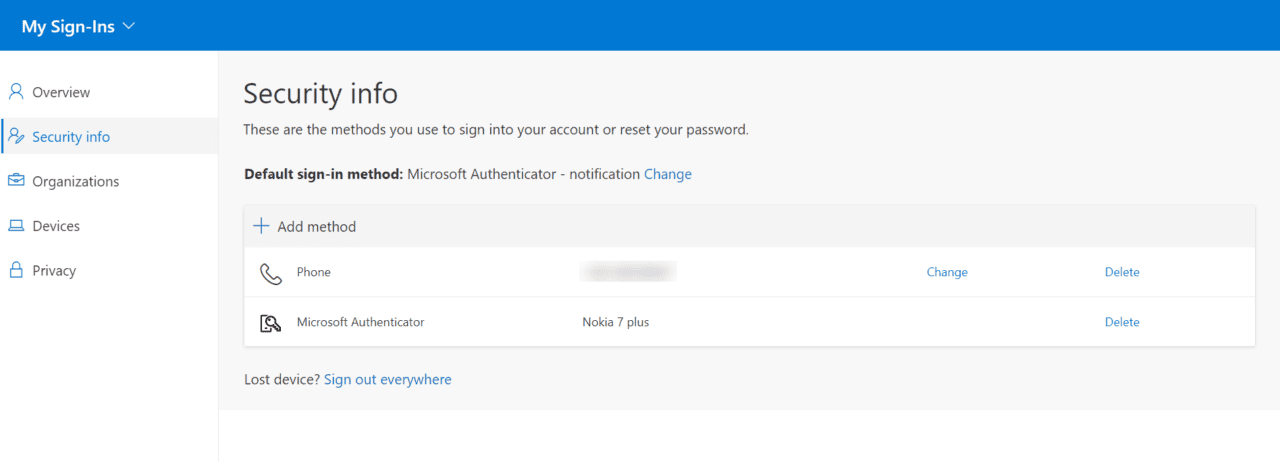
If users need to add Microsoft Authenticator as an authentication method, they can do it here on the My Sign-ins page. Users will need to click Security info in the list of options on the left, click + Add method on the Security info screen, and then follow the on-screen instructions. Users can also choose ‘Microsoft Authenticator – notification’ as the default sign-in method.
Set up passwordless sign-in for the Microsoft Authenticator app
Now that all the prerequisites are in place, you can enable passwordless sign-in for users in your Azure AD tenant.
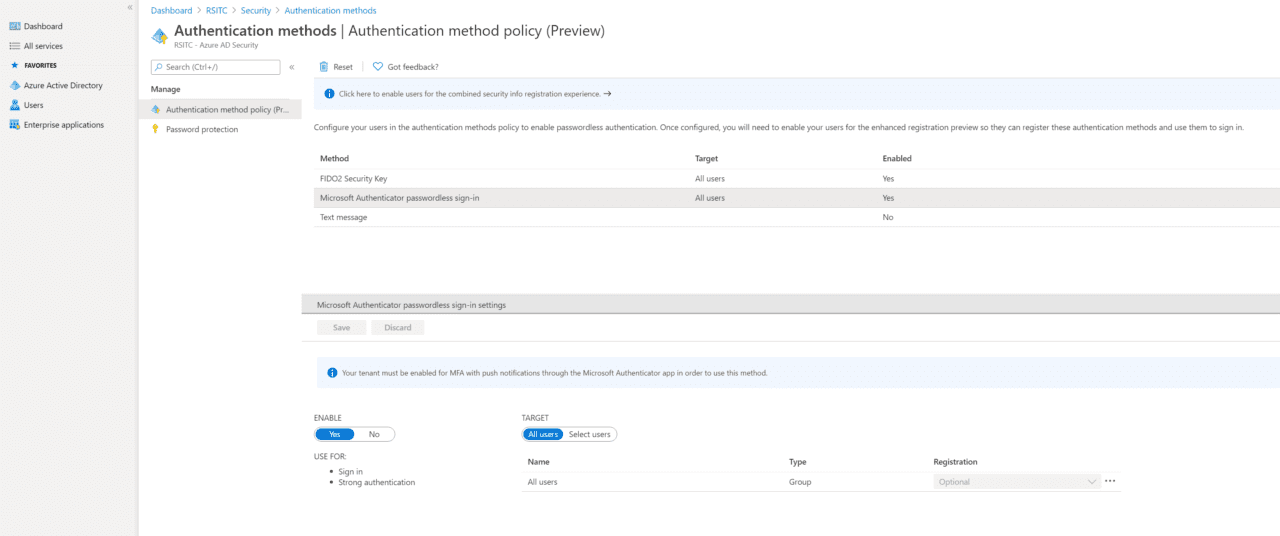
- Back in the Azure AD portal, switch to Authentication methods on the Security
- Click Microsoft Authenticator passwordless sign-in in the list of methods.
- In the Settings pane at the bottom of the portal window, set ENABLE to Yes and TARGET to All users.
Alternatively, you can set TARGET to Select users and enable passwordless sign-in for a group instead of all users in the directory.
- Once you’re done, click Save.
Configure passwordless sign-in on a handset using Microsoft Authenticator
Once your Azure AD tenant is set up for passwordless sign-in, users must set up the feature using the Microsoft Authenticator app. It’s worth noting that passwordless sign-in via the Microsoft Authenticator app can only be configured for one account at a time on a device.
- Open the Microsoft Authenticator app on the handset.
- Select the account you want to configure in the list of accounts.
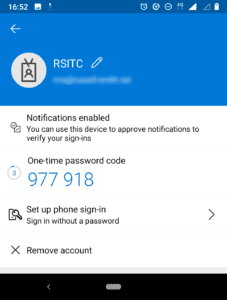
- Now click Set up phone sign-in (Sign in without a password) on the account screen.
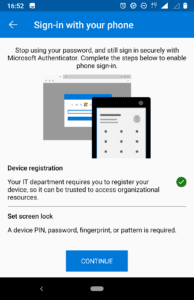
- If you haven’t already done so, the device must be registered with Azure AD. Follow the instructions on screen to register your device.
- Now on the Sign-in with your phone screen, click CONTINUE.
Passwordless sign-in should now be enabled for the account. You can click the account again in the list of accounts to check that ‘Passwordless enabled’ is displayed on the account screen.
Perform a passwordless sign-in
Finally, let’s see whether passwordless sign-in works for the account you configured above.
- In a web browser window, log in to a Microsoft 365 app or service using the account you configured for passwordless sign-in in the previous steps.
- Enter the account username in the sign-in dialog and then click Next.
If you have recently signed in with the account, you may not need to enter the username again. In this case, you can click Send notification in the dialog or click Sign in with another account to change the account that you will use to sign in.
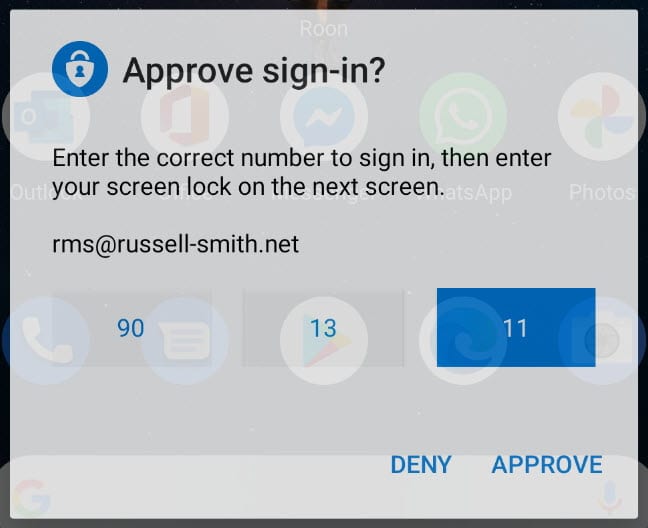
- On the Approve sign in dialog, you’ll see a number. On your handset, you should see a notification requesting you to approve a sign-in. Click the notification.
- In the Approve sign-in dialog on your handset, click the number displayed in the web browser dialog and then click APPROVE. Confirm the action with your screen lock PIN or registered biometric gesture, like a fingerprint.
- Back in the web browser, you should now be signed in to Microsoft 365.
Passwordless sign-in lowers costs and improves security
Initially, it might seem daunting to configure passwordless sign-in. But once you understand where all the configuration ‘bits’ are in Azure AD and the Microsoft Authenticator app, it’s easy to manage. Plus, passwordless sign-in provides a better experience for users over passwords. At least once they’ve gone through the initial setup process.