How do I enable LSA protection in Windows Server 2012 R2 and Windows 8.1?
Windows Server 2012 R2 and Windows 8.1 include updates to the Local Security Authority (LSA), which is responsible for processing local and remote user logins, to help mitigate Pass the Hash (PtH) attacks, in which hackers attempt to capture user password hashes from memory to log in without knowing plaintext passwords.
In Windows 8.1 and Server 2012 R2, lsass.exe can be made a protected process, and hashes are no longer stored in memory to make it much harder for hackers to compromise user credentials. With the exception of Windows 8.1 RT, this new functionality is disabled by default and must be enabled in the registry or using Group Policy. Lsass.exe does not run as a protected process out-of-the-box, because it might cause compatibility problems with some applications, so you must test thoroughly before enabling LSA protection.
LSA Protection and Secure Boot
If computers in your organizations have Secure Boot enabled, i.e. they are running Windows 8.1 or Server 2012 R2 with Secure Boot enabled in the UEFI firmware, you should be aware that when the registry key for LSA protection is set, either using a registry editing tool or Group Policy, the LSA protection setting is also stored in the UEFI firmware and cannot later be modified in Windows. At the time of writing this article, there is no tool to modify this setting in the UEFI firmware, so once set in Windows, there is no means to disable LSA protection if Secure Boot is enabled.
Enable LSA Protection in the Registry
To enable LSA protection in Windows 8.1 or Windows Server 2012 R2, log on to the device as a local administrator:
- Press the Windows key to go to the Start screen and type regedit.
- Right-click regedit in the search results and click Run as administrator at the bottom of the screen.
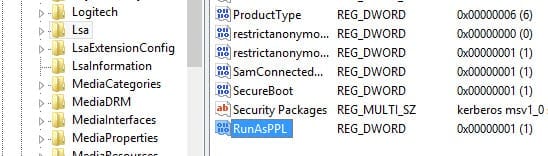
- In the left pane of Registry Editor, expand HKEY_LOCAL MACHINE > SYSTEM > CurrentControlSet > Control > Lsa
- In the right pane, right-click an area of empty space and select New > DWORD (32-bit) Value from the menu.
- In the new value box, type RunAsPPL and press ENTER.
- Now double-click the new RunAsPPL value.
- In the Value data box, type 1 and press OK.
- Close Registry Editor and restart the computer.
Check if Lsass.exe Is Running as a Protected Process
If you want to be sure that lsass.exe is running as a protected process, follow the steps below.
- Open Event Viewer from the Start screen.
- In the left pane of the Event Viewer window, expand Windows Logs and click System.
- Check the System log in the central pane for a Wininit event that shows LSASS.exe was started as a protected process with level: 4.