Enable Unauthenticated Access to a Windows File Share
In today’s Ask the Admin, I’ll explain how unauthenticated access to Windows file shares works.
If you’ve ever tried to configure file share access from one Windows device to another in a workgroup, you’ll know that it can be a bit of a pain. One of the primary advantages of setting up an Active Directory (AD) domain is that configuring access to network resources becomes much easier. Not everybody wants or needs Active Directory. If you don’t have AD, there are a couple of ways to set up access to file shares.
Windows HomeGroup
HomeGroup was first introduced in Windows 7 and makes it easier for users to share file shares and printers on the local area network using a simple wizard-driven process. Microsoft recently announced that it is removing HomeGroup from Windows 10 version 1803, which is due to be released in April. I don’t recommend using HomeGroup because it won’t be supported going forward. Nevertheless, if you do want to use HomeGroup, you can find more information on how to set it up here on Petri: Share Network Resources Using Windows 7 HomeGroup.
The other way to share folders doesn’t differ much from how you might share a folder on a server or device joined to an AD domain. The key difference is how users authenticate to the device hosting the file share. In a workgroup, users must have an account on each device they need to access. For example, if you configure a file share on PC1, any users connecting to PC1 must provide a username and password for an account that exists on PC1. And that has to have permission to access the folder and share.
Passthrough authentication happens when the remote user’s account is duplicated on PC1. I.e. the account they use log in to their own PC also exists on PC1 with exactly the same username and password. In this case, the user connecting to PC1 doesn’t need to provide a username and password when authenticating.
Unauthenticated Access
If you want to set up quick and dirty access to a file share and don’t want to manage access to the share, you can disable password protected sharing to allow unauthenticated access to file shares. In a protected lab environment that doesn’t contain any sensitive data, that might be OK. But in general, I always recommend enforcing authenticated connections, as per the default setting in Windows.
File shares are always accessed using an account. Access is not anonymous but unauthenticated. When password protected sharing is disabled in Windows, the usually disabled built-in guest account is enabled, which by default doesn’t have a password. Once enabled, anyone can connect to a share that has permissions for the Everyone group, Guests, or the built-in guest account.
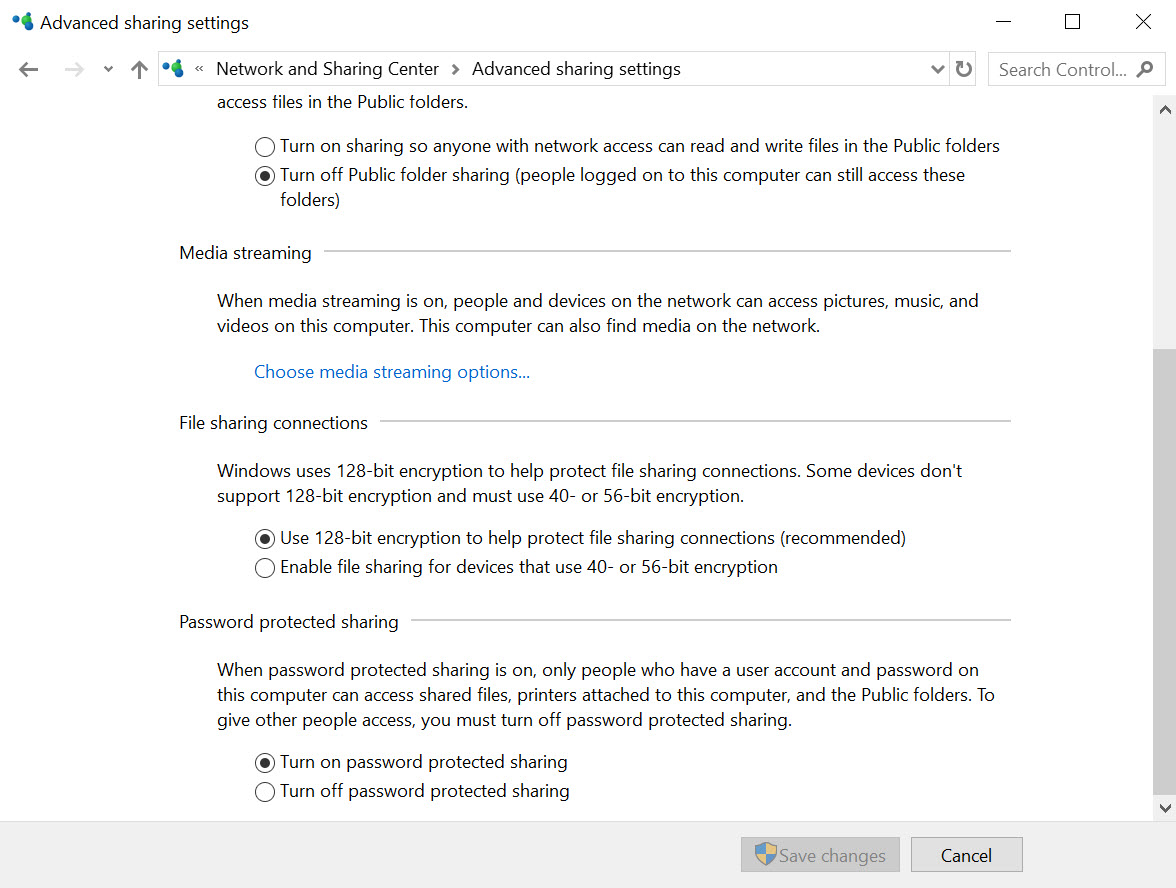
To allow unauthenticated access to file shares, turn off password protected sharing in the Network and Sharing Center.
- Type network into the search box on the taskbar.
- Select Network and Sharing Center from the results.
- On the left of the Network and Sharing Center, click Change advanced sharing settings.
- Expand All Networks at the bottom of the window.
- Check Turn off password protected sharing.
- Click Save changes.
If you turn password protected sharing back on, the built-in guest account remains enabled. If you want to fully reverse the effects of turning off password protected sharing, you’ll need to manually disable the guest account.




