In today’s Ask the Admin, I’ll show you how to quickly create a self-signed certificate.
Self-signed certificates are not recommended for use in production environments, but come in handy for test scenarios where a certificate is a requirement but you don’t have the time or resources to either buy a certificate or deploy your own Public Key Infrastructure (PKI).
But generating self-signed certificates in Windows has traditionally been a bit of a pain, at least if you didn’t have Visual Studio or IIS on hand, as both these products include the ability to generate self-signed certificates. The makecert command line tool was otherwise the “go to” tool, but was only available as part of the Windows SDK, which is a hefty product to download and install just for the sake of using makecert.
Starting in PowerShell version 4.0, Microsoft introduced the New-SelfSignedCertificate cmdlet, making it much easier to create self-signed certificates. To get started, you’ll need a Windows device running PowerShell 4.0 or higher.
- Open a PowerShell prompt. In Windows 10, type powershell in the search dialog on the taskbar, right-click Windows PowerShell in the list of app results, select Run as administrator from the menu and then enter an administrator username and password. The New-SelfSignedCertificate can only install certificates to the My certificate store, and that requires local administrator rights on the device.
- If you’re running a different version of Windows, check the PowerShell version by running the code shown below.
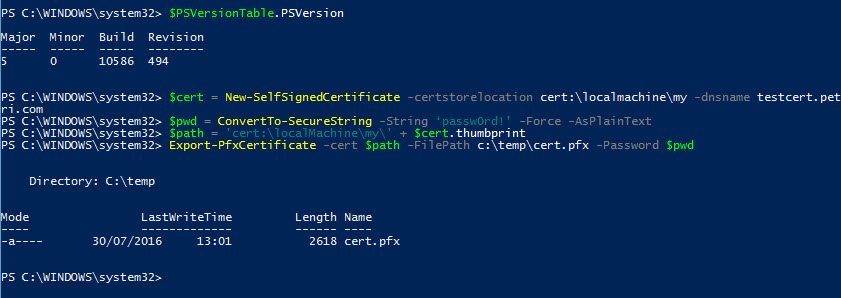
$PSVersionTable.PSVersion
If you need to update PowerShell to version 5, you can download the Windows Management Framework for Windows 7 and Windows 8.1 here.
- Now run the New-SelfSignedCertificate cmdlet as shown below to add a certificate to the local store on your PC, replacing testcert.petri.com with the fully qualified domain name (FQDN) that you’d like to use.
$cert = New-SelfSignedCertificate -certstorelocation cert:\localmachine\my -dnsname testcert.petri.com
The next step is to export a self-signed certificate. But first we’ll need to create a password as shown below:
$pwd = ConvertTo-SecureString -String ‘passw0rd!’ -Force -AsPlainText
Now we can export a self-signed certificate using the Export-PfxCertificate cmdlet. We’ll use the password ($pwd) created above, and create an additional string ($path), which specifies the path to the certificate created with New-SelfSignedCertificate cmdlet.
$path = 'cert:\localMachine\my\' + $cert.thumbprint Export-PfxCertificate -cert $path -FilePath c:\temp\cert.pfx -Password $pwd
Note that the c:\temp directory, or whatever directory you specify in the -FilePath parameter, must already exist. You can now import the cert.pfx file to install the certificate.



