In the security world, the saying that locks keep honest people honest is a hoary old saying. The saying lingers because it is true. One time-tested way to reduce the risk that someone will accidentally or purposefully leak sensitive information is to lock it up. In this article, I will talk about two “locks” that Microsoft provides for helping to reduce information leakage, Azure Information Protection (AIP) and Windows Information Protection (WIP). They are related but different. I will explain when to use each one.
The Disclosure Problem
Information leakage is a real and growing problem for organizations of all sizes. A 2017 Ponemon Institute Study that was funded by IBM estimates the average cost of a data breach worldwide is $3.6 million. The breaches we hear about in the news mostly involve two things, intentional attacks that steal financial data and insiders who leak sensational data about politically sensitive matters. However, many organizations have suffered lower-level breaches when someone forwarded, lost, or leaked a sensitive document or message to someone else who was not supposed to have it. Sometimes, these breaches are accidental and sometimes they are on purpose. Either way, preventing them requires adding more security controls but those controls carry baggage. This baggage can make it harder for users to work and be productive. It can restrict legitimate sharing and make it more difficult to support BYOD. It also requires extra infrastructure. A useful solution for leakage protection has to:
- Allow users and organizations to keep work and personal data on the same devices without mixing them
- Keep unauthorized people from seeing or modifying data
- Protect data when it is stored, in transit, or shared
- Not get in the way when users are trying to work
Of course, besides these problems, we still have the need to protect against other threats such as malware and device theft.
You can break these protection requirements up into four categories, as shown below. AIP and WIP play multiple roles in protecting against these threats.
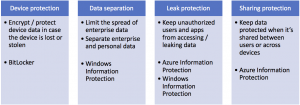
Azure Information Protection
AIP is a cloud-based set of tools that lets you label, classify, and protect documents and messages. Think of it as a superset of the Rights Management System (RMS) functionality offered both on-premises (Active Directory RMS) and as part of Office 365 (Office 365 RMS). The naming is a little confusing because until recently, AIP was known as Azure RMS. The differences are subtle:
- With Office 365 RMS you can protect documents and messages using the Office web and desktop applications. It is included with most enterprise Office 365 SKUs and requires very little setup. You protect items by specifying a template, such as company confidential or do not forward. This controls what the client app will allow a user to do. Let’s refer to this feature level as protection.
- With AD RMS, you can protect documents and messages using on-premises hardware. You do not need any subscriptions or extra licenses. AD RMS uses templates too and it can be connected to Office 365 RMS for hybrid use.
- With AIP, you need EMS or Secure Productive Enterprise SKUs. AIP offers the same template-based protection features as Office 365 RMS using templates. It also adds tools for specifying the classification of confidential, sensitive, secret, etc. The P1 SKU of AIP allows your users to manually classify and visually label files with classification information. The P2 SKU adds the ability to create rules to automatically classify and label objects based on content.
AIP also includes some other features, such as the ability to connect to on-premises Exchange, SharePoint, or AD RMS servers. I will cover these in future articles.
Windows Information Protection
AIP is intended to provide leak protection and sharing protection but it cannot solve one critical problem, mixed data on user devices. Consider your personal tablet, phone, and laptop. If you are synced to your company-provided email or OneDrive for Business account, then your employer’s possibly-sensitive data is mixed in with your personal photos, music, email, etc. If your device is lost, broken, stolen, or you leave the company, you and your employer have different interests. They will want to ensure that their data is securely removed and you will want to ensure that you do not lose your personal data. WIP builds data separation into the operating system so that work data is tagged as such. Work data is automatically encrypted using Windows EFS. It uses a key owned by the organization. The operating system and applications can treat different objects differently, according to whether it is enterprise or personally-owned.
To use WIP, you need three things:
- You need Windows 10 Anniversary Edition or later.
- You need a mobile device management system. Currently, Microsoft supports both SCCM and InTune. Third parties will be supporting WIP policy deployment in the future
- You need A WIP policy that specifies which applications are allowed to work with which types of data. For example, you might allow both enterprise and personal data to be edited in Word but only allow AutoCAD to work with enterprise data.
One key difference between AIP and WIP is that WIP tags data according to its source. When you deploy WIP, your policy also specifies the IP addresses and domain names associated with your intranet. It also specifies which cloud sources you trust. For example, you can allow OneDrive for Business and Dropbox but block Box and Google Drive. When you download or copy a file, WIP knows whether it came from an intranet site, server, or a trusted cloud source. It determines whether it should be tagged as work data or not. In the latter case, it will be marked as personal data.
Getting Started with Information Protection
Both WIP and AIP have complete deployment guides available from Microsoft. They are surprisingly easy to deploy for basic use. In the next articles in this series, I will explain how to set up AIP on clients and in the cloud and how to design and deploy WIP policies. Because you can use these two “locks” together or separately, you can pick the best combination to reduce the risk of accidental or purposeful information leakage.




